Experts warn of mass exploitation of Ivanti Connect Secure VPN flaws
Security Affairs
JANUARY 16, 2024
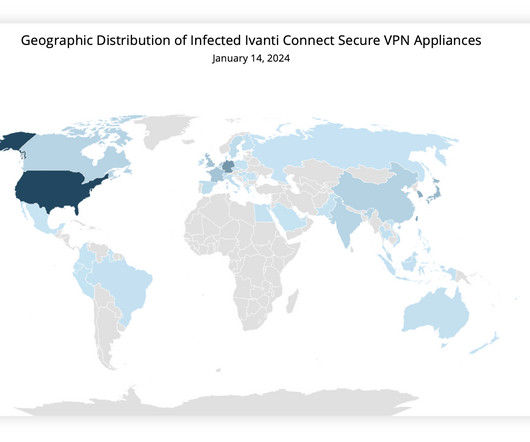
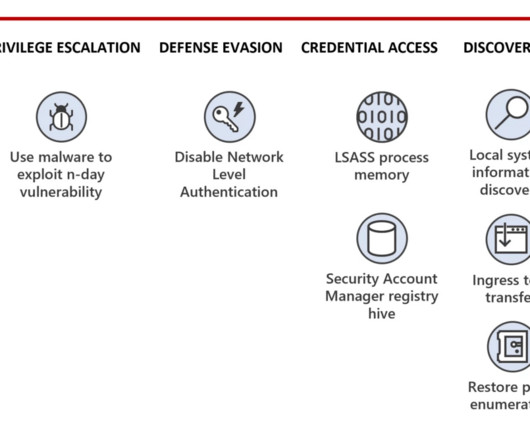
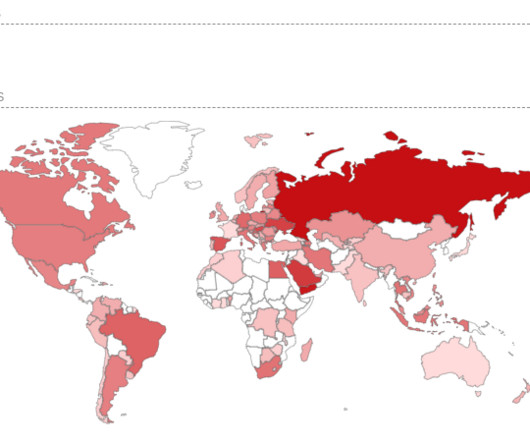
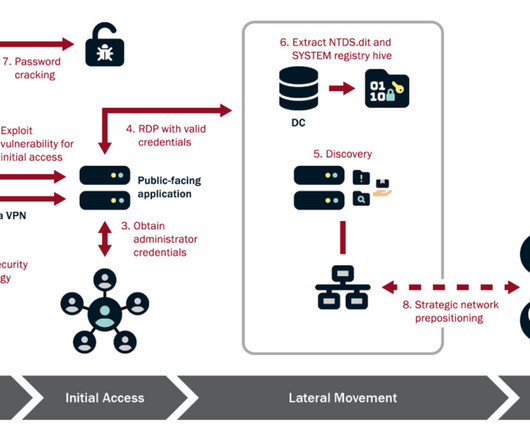
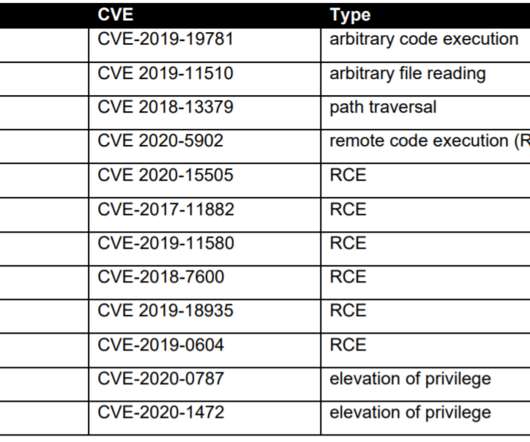
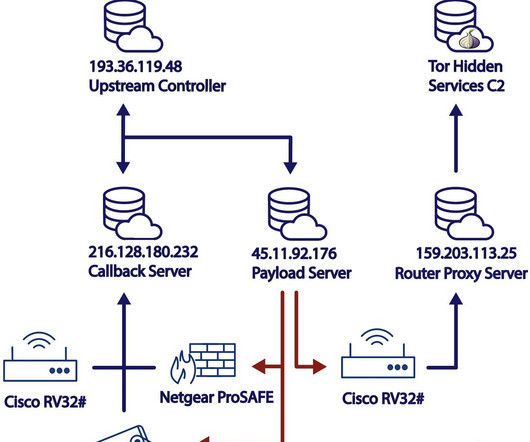
Experts warn that recently disclosed Ivanti Connect Secure VPN and Policy Secure vulnerabilities are massively exploited in the wild. Through forensic analysis of the memory sample, Volexity was able to recreate two proof-of-concept exploits that allowed full unauthenticated command execution on the ICS VPN appliance.






































Let's personalize your content