Getting the Most Value Out of the OSCP: After the Exam
Security Boulevard
JUNE 2, 2025
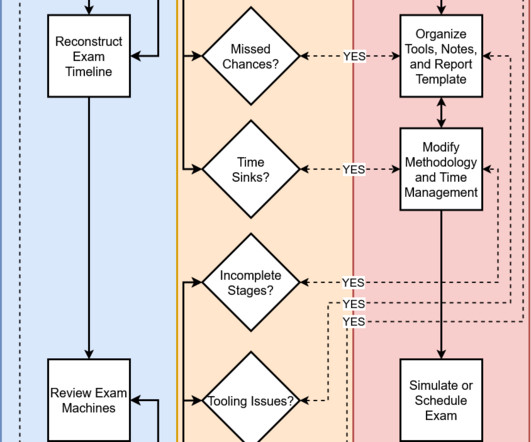
Introduction Throughout this series, Ive shared practical advice for PEN-200: Penetration Testing with Kali Linux students seeking to maximize the professional, educational, and financial value of pursuing the Offensive Security Certified Professional (OSCP) certification.
























Let's personalize your content