How Solid Protocol Restores Digital Agency
Schneier on Security
JULY 24, 2025
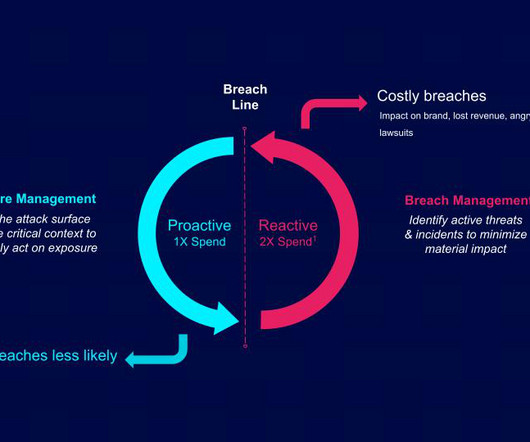
Your personal information is scattered across hundreds of locations: social media companies, IoT companies, government agencies, websites you have accounts on, and data brokers you’ve never heard of. The current state of digital identity is a mess. It’s both redundant and inconsistent. Let’s take healthcare as an example.

















































Let's personalize your content