Add Security, Not Headaches, to the SDLC
Security Boulevard
SEPTEMBER 20, 2021
How to integrate security into the SDLC successfully. cumbersome security analysis tools and a strong drive to reach the market quickly. For things to improve, developers need better code analysis tools make implementing security into the software development lifecycle (SDLC) much easier.


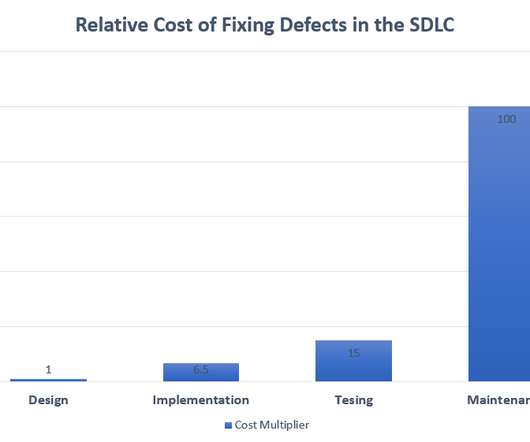



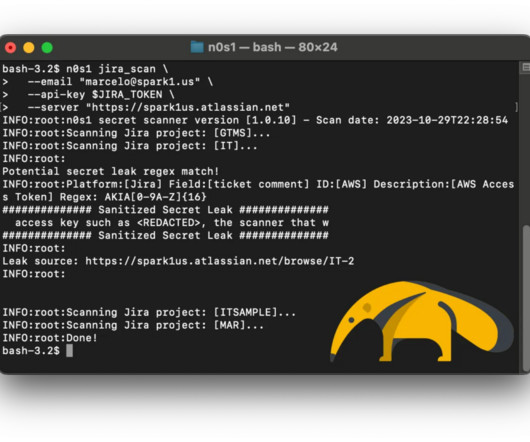




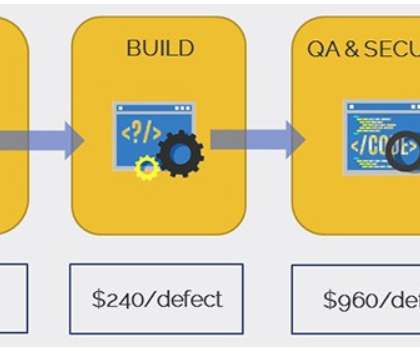














Let's personalize your content