Netgear Routers' Flaws Expose Users to Malware, Remote Attacks, and Surveillance
The Hacker News
MAY 12, 2023
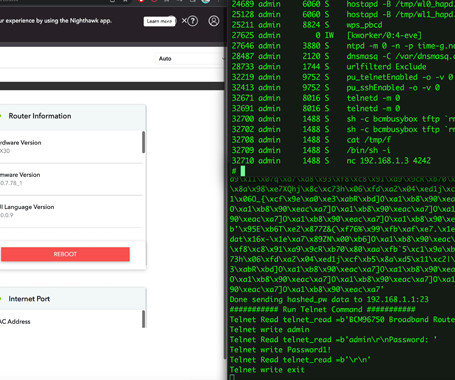
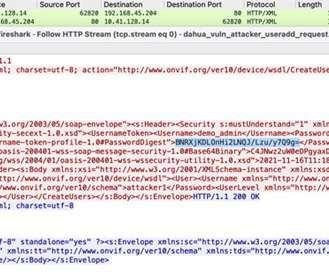
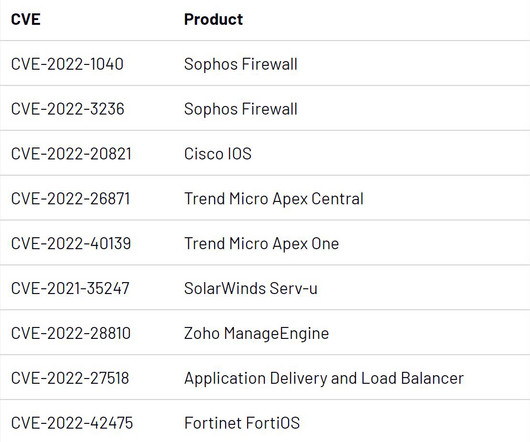
Successful exploits could allow attackers to monitor users' internet activity, hijack internet connections, and redirect traffic to malicious websites or inject malware into network traffic," Claroty security researcher Uri Katz said in a









































Let's personalize your content