How to Maximize the Value of Penetration Tests
eSecurity Planet
JUNE 23, 2023
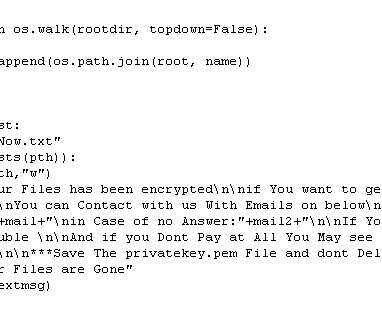
All organizations should perform penetration tests, yet many worry about not receiving the full value of their investment. Organizations have two choices: perform penetration tests with their internal teams, or hire an external vendor and find ways to lower costs.


















































Let's personalize your content