Private Internet Access VPN Black Friday Deal 2023: Embark on a Cybersecurity Odyssey
SecureBlitz
NOVEMBER 13, 2023
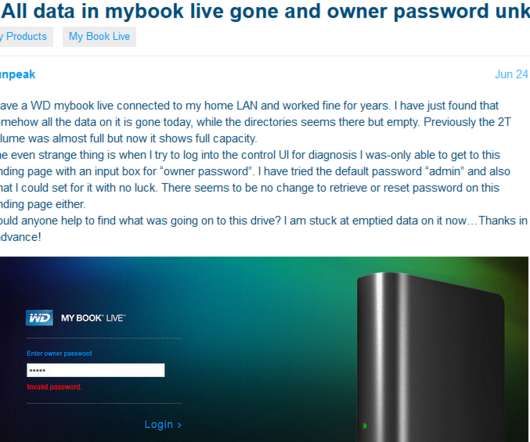
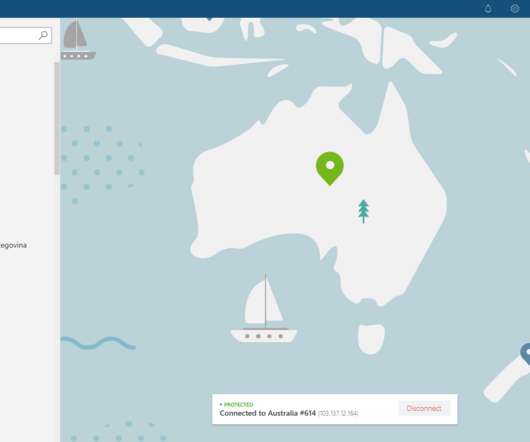
In this post, I will reveal the Private Internet Access VPN Black Friday deal. Welcome, cyber guardians of SecureBlitz, to a cybersecurity revolution brought to you by Private Internet Access VPN's Black Friday deal extravaganza!















































Let's personalize your content