Brits Ban Default Passwords — and More IoT Stupidity
Security Boulevard
APRIL 30, 2024
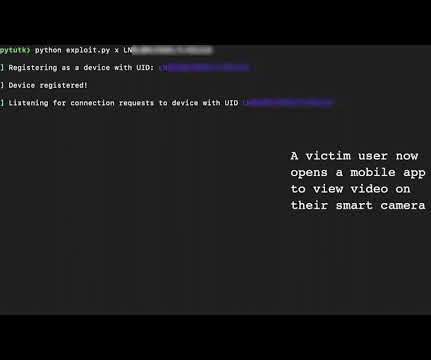
The post Brits Ban Default Passwords — and More IoT Stupidity appeared first on Security Boulevard. The UK’s Product Security and Telecommunications Infrastructure Act aims to improve the security of net-connected consumer gear.
















































Let's personalize your content