A Day in the Life of a Prolific Voice Phishing Crew
Krebs on Security
JANUARY 7, 2025
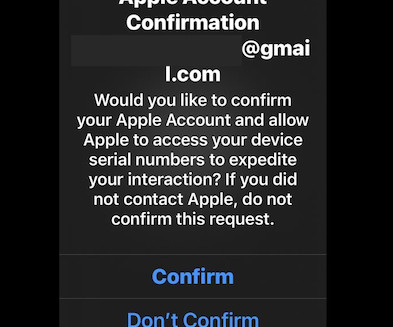
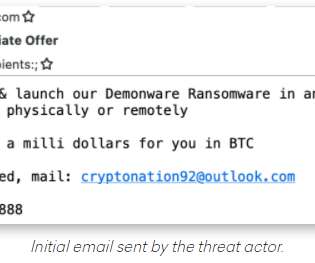
Each participant in the call has a specific role, including: -The Caller: The person speaking and trying to social engineer the target. In the first step of the attack, they peppered the target’s Apple device with notifications from Apple by attempting to reset his password. “Password is changed,” the man said.









































Let's personalize your content