Synthetic Sabotage: How AI Tools Are Fueling Tailored Phishing Campaigns at Scale
SecureWorld News
APRIL 28, 2025
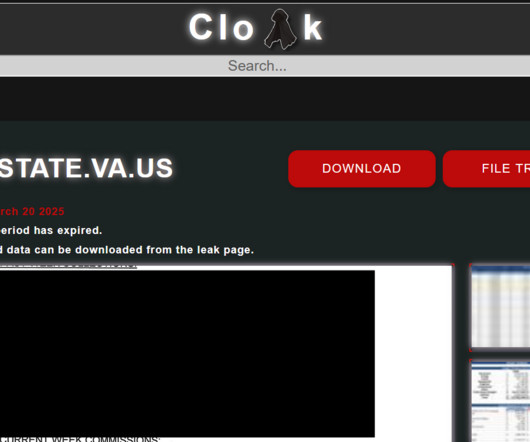
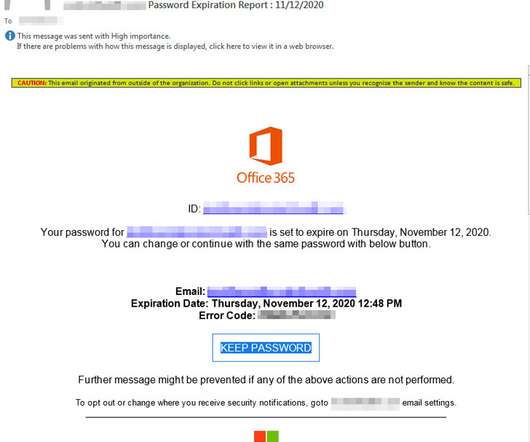
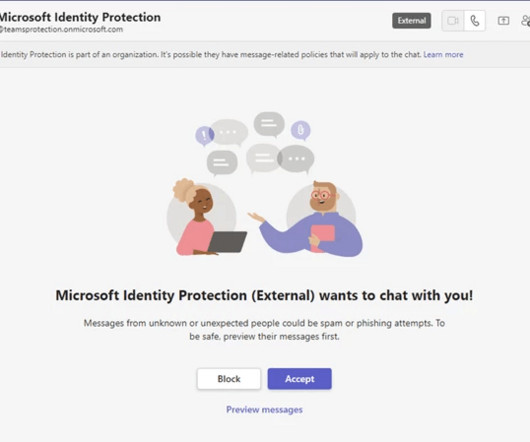
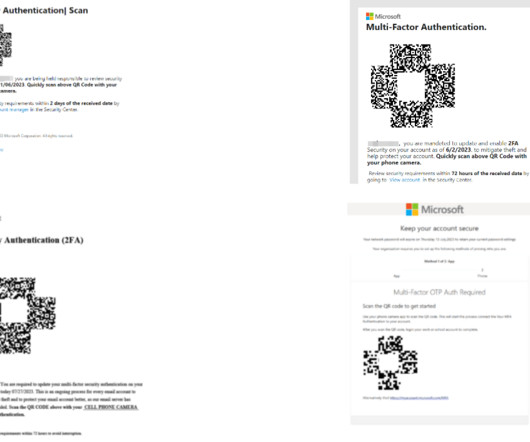
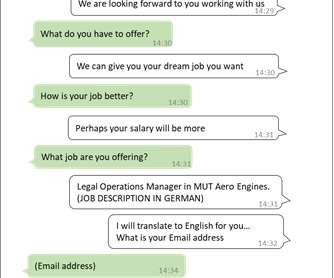
The phishing game has evolved into synthetic sabotage a hybrid form of social engineering powered by AI that can personalize, localize, and scale attacks with unnerving precision. The quiet revolution of phishing-as-a-service (PhaaS) If you haven't noticed by now, phishing has gone SaaS.











































Let's personalize your content