6 Best Open Source IAM Tools in 2024
Tech Republic Security
FEBRUARY 22, 2024
Explore the top open source IAM (Identity and Access Management) tools, their features and how they can enhance your organization's security and access control.
This site uses cookies to improve your experience. By viewing our content, you are accepting the use of cookies. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country we will assume you are from the United States. View our privacy policy and terms of use.

 open-source-tools
open-source-tools 
Tech Republic Security
FEBRUARY 22, 2024
Explore the top open source IAM (Identity and Access Management) tools, their features and how they can enhance your organization's security and access control.
The Hacker News
FEBRUARY 22, 2024
A recently open-sourced network mapping tool called SSH-Snake has been repurposed by threat actors to conduct malicious activities. SSH-Snake is a self-modifying worm that leverages SSH credentials discovered on a compromised system to start spreading itself throughout the network," Sysdig researcher Miguel Hernández said.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
The Hacker News
FEBRUARY 16, 2024
Google has announced that it's open-sourcing Magika, an artificial intelligence (AI)-powered tool to identify file types, to help defenders accurately detect binary and textual file types.

We Live Security
FEBRUARY 29, 2024
Here’s how the blue team wards off red teamers and a few open-source tools it may leverage to identify chinks in the corporate armor

eSecurity Planet
OCTOBER 18, 2021
Over the past quarter of a century, the open source movement has gone from strength to strength. But that success and the openness inherent in the community have led to a major challenge – security. To make matters worse, the open source world prides itself on openness and transparency. WhiteSource.

Penetration Testing
DECEMBER 4, 2023
MetaHub MetaHub is an open-source security tool for context-based security vulnerability management. It focuses on... The post metahub: open-source security tool for context-based security vulnerability management appeared first on Penetration Testing.

Bleeping Computer
OCTOBER 14, 2022
Cybersecurity and Infrastructure Security (CISA) agency has announced RedEye, an open-source analytic tool for operators to visualize and report command and control (C2) activity. [.].

eSecurity Planet
APRIL 15, 2022
Vulnerability assessment tools usually scan applications for known vulnerabilities. While there are premium products, organizations often leverage the benefits of robust open-source technologies to save money. Kali Linux can save a lot of time and remove the hassle of installing each tool separately.
InfoWorld on Security
DECEMBER 8, 2023
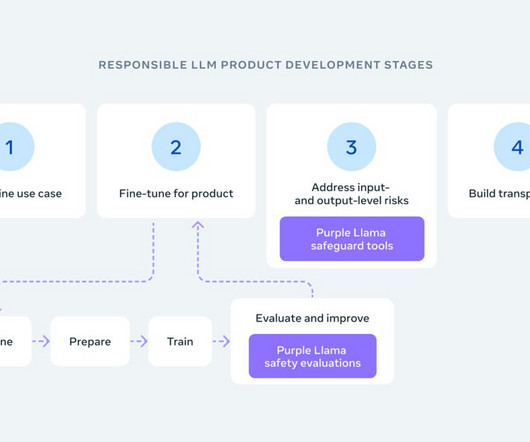
Meta has introduced Purple Llama, a project dedicated to creating open-source tools for developers to evaluate and boost the trustworthiness and safety of generative AI models before they are used publicly.
Security Boulevard
MARCH 15, 2022
This Nexus platform update will help developers more easily remediate vulnerable open source usage across their projects. The post New Developer Tools for Open Source Dependency Management appeared first on Security Boulevard.
Security Boulevard
DECEMBER 20, 2021
WhiteSource has made available an open source tool to detect vulnerable instances of Log4j logging software. Rami Sass, WhiteSource CEO, said WhiteSource is also testing an extension to that command-line interface (CLI) tool that will enable IT teams.

CSO Magazine
JUNE 28, 2021
Open source intelligence (OSINT) is the practice of collecting information from published or otherwise publicly available sources. Open source in this context doesn't refer to the open-source software movement , although many OSINT tools are open source; instead, it describes the public nature of the data being analyzed.

Penetration Testing
NOVEMBER 1, 2023
unshackle – Password Bypass Tool Unshackle is an open-source tool to bypass Windows and Linux user passwords from a bootable USB based on Linux.

Security Boulevard
FEBRUARY 17, 2022
Open source tools offer software that–in addition to being free–has had its code reviewed by numerous users. The post Open Source Favorites: 7 Security Tools You Should Know appeared first on Hurricane Labs. The post Open Source Favorites: 7 Security Tools You Should Know appeared first on Hurricane Labs.

Appknox
AUGUST 30, 2022
When choosing automated mobile app security testing tools, mobile app development companies have two options: open-source and commercialized tools. But which one should you go for? Or, to be more precise, which one’s cheaper? If you have these questions on your mind, you’ve come to the right place.
Security Boulevard
NOVEMBER 21, 2022
As the new year fast approaches, it’s time to consider what Kubernetes open source tools you need in 2023. . The post Top 4 Kubernetes Open Source Tools You Need in 2023 appeared first on Security Boulevard.

Heimadal Security
FEBRUARY 10, 2023
Are you on the lookout for threat-hunting tools? While traditional defense methods generally investigate threats after they […] The post 10 Free & Open Source Threat-Hunting Tools for 2023 appeared first on Heimdal Security Blog. If so, you’ve come to the right place.

Heimadal Security
JULY 16, 2021
You might think about using some free and open source cybersecurity tools for your business needs as they have reduced costs. Many of the tools perform as expected and give your security team or […]. Many of the tools perform as expected and give your security team or […].

eSecurity Planet
AUGUST 8, 2023
SandboxAQ today introduced an open-source cryptography management framework built for the post-quantum era. The open-source solution can be embedded into internal applications and commercial software. government agencies, global banks, telcos, and tech companies. You can unsubscribe at any time.

Security Boulevard
FEBRUARY 2, 2023
The post Project Highlights for World Open Source Day: My Open Source Tools appeared first on Security Boulevard.

Bleeping Computer
MAY 1, 2022
The Open Source Security Foundation (OpenSSF), a Linux Foundation-backed initiative has released its first prototype version of the 'Package Analysis' tool that aims to catch and counter malicious attacks on open source registries.
Security Affairs
MARCH 17, 2022
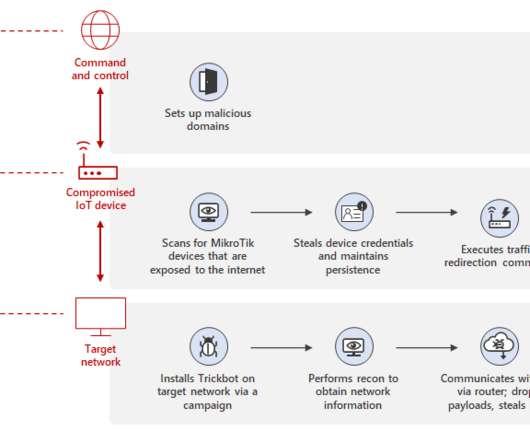
Microsoft released an open-source tool to secure MikroTik routers and check for indicators of compromise for Trickbot malware infections. “This analysis has enabled us to develop a forensic tool to identify Trickbot-related compromise and other suspicious indicators on MikroTik devices. . Pierluigi Paganini.
Bleeping Computer
SEPTEMBER 29, 2021
Facebook today open-sourced a static analysis tool its software and security engineers use internally to find potentially dangerous security and privacy flaws in the company's Android and Java applications. [.].

Security Affairs
APRIL 17, 2023
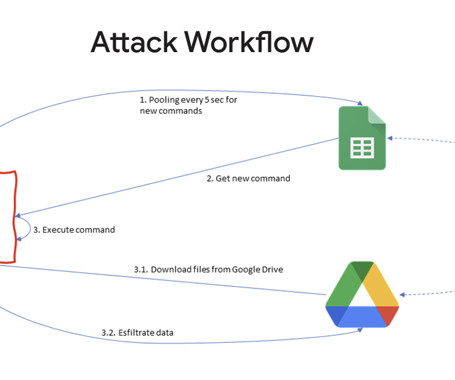
China-linked APT41 group used the open-source red teaming tool GC2 in an attack against a Taiwanese media organization. The final payload was the Go-written GC2 tool that gets commands from Google Sheets and exfiltrates data to Google Drive. HOODOO’s use of GC2 is an example of this trend. ” continues the report.

Security Affairs
MAY 11, 2021
Google has released a new open-source tool called cosign that could allow administrators to sign and verify the container images. Google has released a new open-source tool called cosign that allows to sign, verify container images, it was developed to make signatures invisible infrastructure.

CSO Magazine
MARCH 23, 2022
Comcast is releasing a new software tool, xGitGuard, as an open source project to the community at large. The tool is designed to proactively search the open source repositories of GitHub for code that was supposed to remain proprietary.
Security Affairs
APRIL 10, 2020
Sophos announced the public release of the source code of the sandbox-based isolation program Sandboxie. Sophos is going to release the Windows sandbox-based isolation program Sandboxie in open source. “Sandboxie has long been a favorite sandbox-based isolation tool since its original release over fifteen years ago.

Security Boulevard
FEBRUARY 6, 2023
The key is choosing thoughtfully developed tech and tools; when we can’t find what we need, we create it ourselves! […] The post Open Source Tools: From Our Lab to Your Fingertips appeared first on Praetorian. The post Open Source Tools: From Our Lab to Your Fingertips appeared first on Security Boulevard.

The Hacker News
MAY 1, 2022
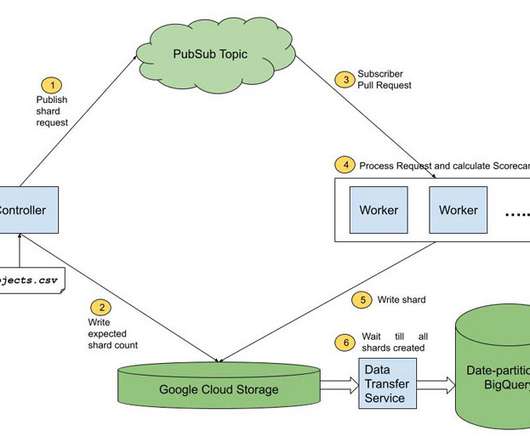
The Open Source Security Foundation (OpenSSF) has announced the initial prototype release of a new tool that's capable of carrying out dynamic analysis of all packages uploaded to popular open source repositories.
The Hacker News
JULY 2, 2021
Google has launched an updated version of Scorecards, its automated security tool that produces a "risk score" for open source initiatives, with improved checks and capabilities to make the data generated by the utility accessible for analysis.

Security Boulevard
DECEMBER 16, 2021
Contrast is releasing SafeLog4j, a free and open-source, general purpose tool that can detect/verify vulnerable log4j applications and protect them. The utility works with user-developed and third party applications, does not require source code, and works against WAF bypass attacks.

Malwarebytes
MAY 9, 2022
The Open Source Security Foundation (OpenSSF), a collective of industry leaders aimed at improving the security of open-source software (OSS), recently announced the release of a prototype tool that scans for malicious packages in open source repositories.
The Hacker News
APRIL 17, 2023
A Chinese nation-state group targeted an unnamed Taiwanese media organization to deliver an open source red teaming tool known as Google Command and Control (GC2) amid broader abuse of Google's infrastructure for malicious ends.

Dark Reading
AUGUST 10, 2022
The new open source tools are designed to help defense, identity and access management, and security operations center teams discover vulnerable network shares.

Security Affairs
FEBRUARY 4, 2022
Retail giant Target is going to open-source an internal tool, dubbed Merry Maker , designed to detect e-skimming attacks. Retail giant Target announced the release in open-source of an internal tool, dubbed Merry Maker , designed to detect e-skimming attacks. ” reads the description of the project.
Security Affairs
FEBRUARY 27, 2023
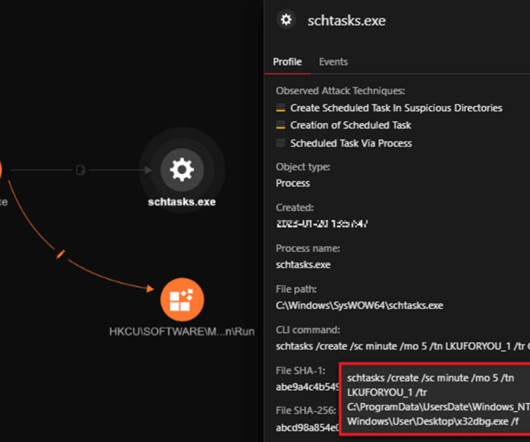
Researchers detailed a new wave of attacks distributing the PlugX RAT disguised as a legitimate Windows debugger tool. Trend Micro uncovered a new wave of attacks aimed at distributing the PlugX remote access trojan masqueraded as an open-source Windows debugger tool called x32dbg.

Dark Reading
AUGUST 1, 2023
The open source ecosystem for offensive and defensive security technologies is flourishing, giving security teams access to a wide range of tools to do their jobs.

Security Boulevard
APRIL 14, 2021
Tel Aviv – Spectral, the developer-first cybersecurity company, announced the release of Teller, an open-source tool that helps developers securely retrieve and use sensitive access details. Teller is the first open source secret manager to solve the “last mile.

Security Affairs
AUGUST 22, 2020
Adobe has released an open-source tool, dubbed Stringlifier, that allows users to identify randomly generated strings in any plain text, it can be used to sanitize logs. Adobe has released an open-source tool, dubbed Stringlifier, which was designed to identify randomly generated strings in any plain text.
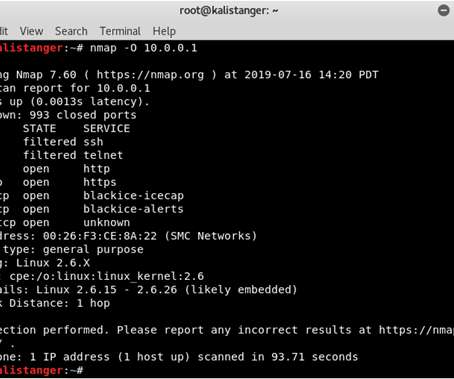
CompTIA on Cybersecurity
SEPTEMBER 29, 2021
Tools and protocols go hand-in-hand. Take a look at what open-source tools work when you’re pen testing.

Acunetix
FEBRUARY 16, 2021
With the immense popularity of open-source software such as Linux, WordPress, or Magento, you might wonder why the situation is so different in the world of web application security. Let’s try to compare open-source vulnerability scanners with commercial solutions and it will soon be clear. appeared first on Acunetix.

Security Boulevard
FEBRUARY 16, 2021
With the immense popularity of open-source software such as Linux, WordPress, or Magento, you might wonder why the situation is so different in the world of web application security. Let’s try to compare open-source vulnerability scanners with commercial solutions and it will soon be clear. appeared first on Acunetix.
Bleeping Computer
JANUARY 17, 2024
Open source solutions allow organizations to customize and adapt their cybersecurity infrastructure to their specific needs. Learn more from @wazuh on building open source cybersecurity infrastructure. [.]

Tech Republic Security
DECEMBER 1, 2021
This won't replace antivirus software, but it can help you detect problems much more efficiently and allows more customization. Here's how to install it on Mac, Windows and Linux.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?

Let's personalize your content