World Password Day 2024: A Wake-Up Call for Better Password Practices
SecureWorld News
MAY 2, 2024
In our digitally connected world, passwords are the gateway to protecting our online lives—from email and social media accounts to banking and private data. Yet, many of us still use alarmingly weak passwords or reuse the same ones across multiple sites, putting our digital identities at severe risk.



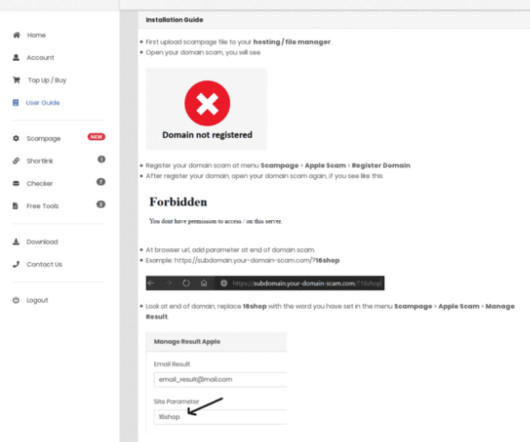















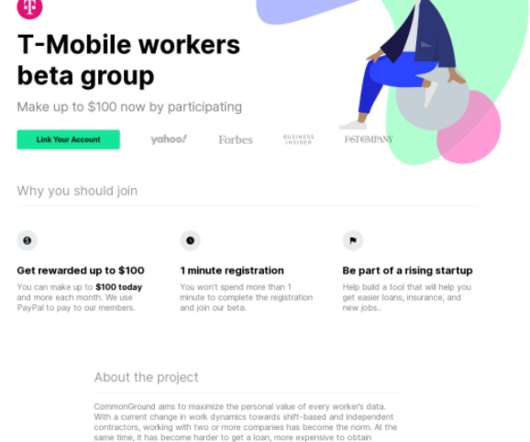




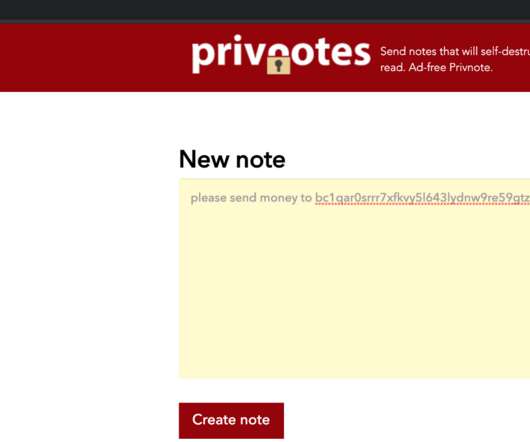

























Let's personalize your content