A Call for Change in Physical Security
Dark Reading
NOVEMBER 16, 2020
We're at an inflection point. The threats we face are dynamic, emerging, and global. Are you ready?
This site uses cookies to improve your experience. By viewing our content, you are accepting the use of cookies. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country we will assume you are from the United States. View our privacy policy and terms of use.

 physical-security a-call-for-change-in-physical-security
physical-security a-call-for-change-in-physical-security 
Dark Reading
NOVEMBER 16, 2020
We're at an inflection point. The threats we face are dynamic, emerging, and global. Are you ready?

Schneier on Security
DECEMBER 15, 2023
In 2016, I wrote about an Internet that affected the world in a direct, physical manner. Arguing with customer service—on chat—for service changes and refunds. But these AIs will interact with the physical world as well, first controlling robots and then having those robots as part of them. This is the easy stuff.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

SecureWorld News
MAY 7, 2024
While the intrusions so far have largely caused nuisance impacts like manipulating equipment settings, the alert warns that hackers potentially have capabilities to pose major physical threats to insecure OT environments they access. " Multiple U.S. The fact sheet is being distributed through a partnership of the U.S.

Krebs on Security
FEBRUARY 26, 2023
But it’s worth revisiting how this group typically got in to targeted companies: By calling employees and tricking them into navigating to a phishing website. Media coverage understandably focused on GoDaddy’s admission that it suffered three different cyberattacks over as many years at the hands of the same hacking group.
Krebs on Security
MAY 9, 2023
Microsoft today released software updates to fix at least four dozen security holes in its Windows operating systems and other software, including patches for two zero-day vulnerabilities that are already being exploited in active attacks. However, as the SANS Internet Storm Center points out , the attack vector for this bug is local.

The Last Watchdog
APRIL 1, 2024
Related: Data privacy vs data security However, this remains a novel concept at most companies. The report, titled “ Embed Cybersecurity And Privacy Everywhere To Secure Your Brand And Business ,” argues for a paradigm shift. Shey Shey: This is something that calls for a maturity assessment.

The Last Watchdog
JULY 24, 2023
Related: Satya Nadella calls for facial recognition regulations Historically, this relationship has been effective from both the user experience and host perspectives; passwords unlocked a world of possibilities, acted as an effective security measure, and were simple to remember. That all changed rather quickly.

Malwarebytes
MAY 10, 2024
A cybercriminal called Menelik posted the following message on the “Breach Forums” site: “The data includes 49 million customer and other information of systems purchased from Dell between 2017-2024. Change your password. Change your password. You can make a stolen password useless to thieves by changing it.

Krebs on Security
APRIL 29, 2022
Google said this week it is expanding the types of data people can ask to have removed from search results, to include personal contact information like your phone number, email address or physical address. Google has for years accepted requests to remove certain sensitive data such as bank account or credit card numbers from search results.

Daniel Miessler
SEPTEMBER 13, 2020
This is easier to see in the information security world. We call that patching. And not the worker-prep kind of education where you learn how to be an obedient and productive office worker, but the kind that teaches the fundamentals of how things work—from physics to psychology, and from physiology to philosophy.

The Last Watchdog
AUGUST 8, 2022
Digital twins are a digital representation of reality , either in physical or process form. They might be able to find the most vulnerable spots in the physical structure to stage a terrorist attack. They might be able to find the most vulnerable spots in the physical structure to stage a terrorist attack.

Identity IQ
OCTOBER 27, 2023
They can do this using your physical card or stealing your credit card number and PIN. Of those many ways, they can get thrown into two categories: Card Present Fraud Card present fraud refers to when someone steals or finds your physical credit card and uses it to make purchases.
Krebs on Security
MAY 19, 2021
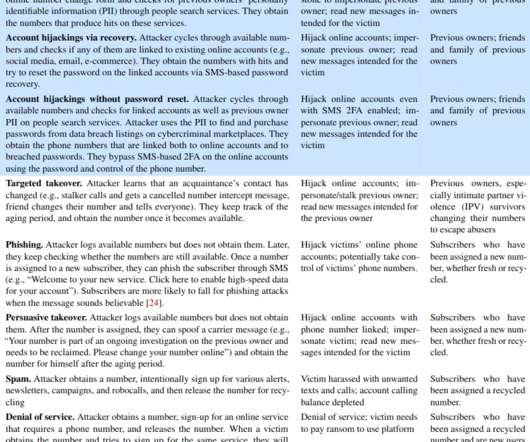
“On postpaid interfaces, Verizon already has safeguards and T-Mobile does not even support changing numbers online,” the researchers wrote. “On postpaid interfaces, Verizon already has safeguards and T-Mobile does not even support changing numbers online,” the researchers wrote.

Krebs on Security
AUGUST 30, 2022
A recent spate of SMS phishing attacks from one cybercriminal group has spawned a flurry of breach disclosures from affected companies, which are all struggling to combat the same lingering security threat: The ability of scammers to interact directly with employees through their mobile devices.

Joseph Steinberg
FEBRUARY 2, 2022
The reason that such a major threat exists is simple – much of today’s data relies on the security of what are known as asymmetric encryption algorithms, and such algorithms rely for their security on the fact that the mathematics that they use to encrypt cannot easily be reversed in order to decrypt.
Krebs on Security
APRIL 6, 2021
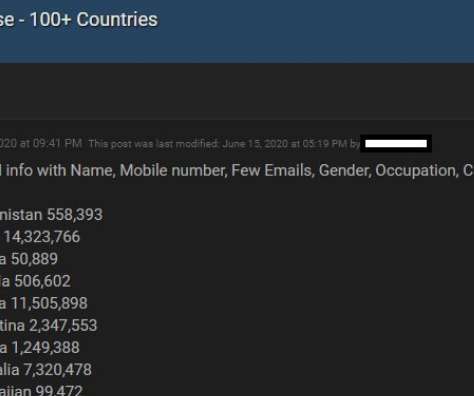
Facebook says the data was collected before 2020 when it changed things to prevent such information from being scraped from profiles. Ne’er-do-wells leaked personal data — including phone numbers — for some 553 million Facebook users this week. billion active monthly users. According to a Jan. According to a Jan.

Krebs on Security
MARCH 16, 2021
SMS text messages were already the weakest link securing just about anything online, mainly because there are tens of thousands of employees at mobile stores who can be tricked or bribed into swapping control over a mobile phone number to someone else. While adding a number, Sakari provides the Letter of Authorization for the user to sign.

The Last Watchdog
JULY 10, 2023
I had a wide-ranging conversation with NTT Research President & CEO Kazu Gomi about an ambitious initiative called Innovative Optical and Wireless Network ( IOWN ) that aims to develop next-generation networks and computations. In short, the mighty integrated circuit is maxed out. Here are my takeaways.

Security Affairs
FEBRUARY 3, 2020
Cybercriminals are planting so-called “sleepers” in cleaning companies so that they can physically access IT infrastructure and hack them. The alert was launched by a senior p olice officer, cyber criminals are p lanting so-called “sleepers” in cleaning companies so that they can gau physical access IT infrastructure and hack them.

Malwarebytes
FEBRUARY 27, 2023
Some victims say they were physically assaulted and threatened into revealing their passcode. Once the phone has gone, the thieves log in to the person's Apple ID and change it to something of their own. Even the new security key meant to protect Apple IDs doesn't prevent anyone from making account changes using only a passcode.

Thales Cloud Protection & Licensing
FEBRUARY 21, 2024
Unfortunately, API attacks are increasing as vectors for security incidents. In this blog, we will explain the unique data security challenges for Telcos and three ways how both Thales and Red Hat can help them protect against future API attacks. In particular, the Telcom industry has fallen victim to several high-profile API attacks.

Krebs on Security
JANUARY 30, 2024
Multiple trusted sources told KrebsOnSecurity that Sosa/King Bob was a core member of a hacking group behind the 2022 breach at Twilio , a company that provides services for making and receiving text messages and phone calls. Multiple security firms soon assigned the hacking group the nickname “ Scattered Spider.”

Security Through Education
FEBRUARY 20, 2024
Pre-Internet Era: In the pre-internet era, social engineering primarily relied on interpersonal communication and physical access. Techniques included impersonation, dumpster diving for sensitive information, and manipulating individuals through phone calls (also known as vishing).

SecureWorld News
JANUARY 10, 2024
I have always known about physical security keys, also called hard tokens, but never actually used one despite my curiosity. So, I was kind of excited when I got my hands on two cool things: a YubiKey 5 and a Google Titan security key. Let's hope to see some change in this department in 2024.

LRQA Nettitude Labs
MARCH 22, 2023
A covert entry assessment is a physical security assessment in which penetration testers try to gain access to sensitive or valuable data, equipment, or a certain location on a target site, without being detected. In all types of social engineering, the explanation for an email, call, or physical visit is called a pretext.
Krebs on Security
APRIL 28, 2020
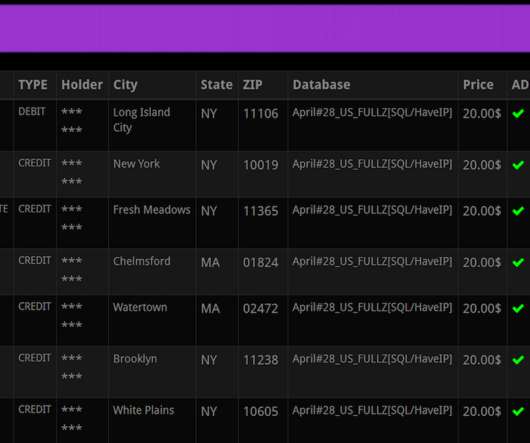
You may have heard that today’s phone fraudsters like to use use caller ID spoofing services to make their scam calls seem more believable. Last week, KrebsOnSecurity told the harrowing tale of a reader (a security expert, no less) who tried to turn the tables on his telephonic tormentors and failed spectacularly.

Security Affairs
FEBRUARY 10, 2022
Verify the call by dialing the customer service line of your mobile carrier. Be aware of any changes in SMS-based connectivity. Use strong multi-factor authentication methods such as biometrics, physical security tokens, or standalone authentication applications to access online accounts.

CyberSecurity Insiders
JANUARY 6, 2023
By Tyler Reguly, senior manager, security R&D at cybersecurity software and services provider Fortra. Time for change. First launched in 2004 and updated most recently in 2018, the PCI Data Security (PCI DSS) standard is continually updated to reflect the evolving challenges of the cyberthreat landscape. In fact, the U.S.

Krebs on Security
NOVEMBER 22, 2021
Image: Abnormal Security. The brazen approach targeting disgruntled employees was first spotted by threat intelligence firm Abnormal Security , which described what happened after they adopted a fake persona and responded to the proposal in the screenshot above. Please don’t harm Sociogram’s reputation,” Medayedupin pleaded. “I
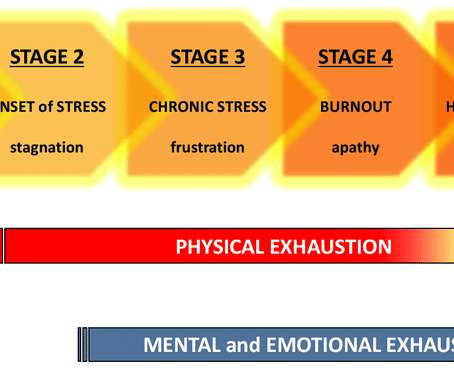
Security Through Education
DECEMBER 8, 2021
According to the Chartered Institute of Information Security (CIIS) 2020/21 State of the Profession report, job stress keeps 51% of cybersecurity professionals up at night. Of the hundreds of security professionals surveyed, the majority mentioned that stress and burnout have become a major issue during the COVID-19 pandemic.

Approachable Cyber Threats
FEBRUARY 8, 2023
The world is changing, and the banking industry is evolving too. Modern banking is all about the “digital experience” and moving faster - so we call it “Digital Banking.” Card skimming occurs when criminals physically install devices on ATMs or other point-of-sales to capture debit/credit card details entered during transactions.

SecureWorld News
MAY 13, 2021
million dollar information governance report for the company which uncovered, “a patchwork of poorly connected and secured systems.”. Now a powerful voice is calling for that to change. So what has changed since then? Which company was this person speaking about? Colonial Pipeline. The person speaking authored a $1.8

Krebs on Security
SEPTEMBER 28, 2021
When scanned, an AirTag in Lost Mode will present a short message asking the finder to call the owner at at their specified phone number. The vulnerability was discovered and reported to Apple by Bobby Rauch , a security consultant and penetration tester based in Boston. But your average Good Samaritan might not know this.

Krebs on Security
MARCH 8, 2022
“The business services we provide are extremely small and very limited as is our physical presence. . “The business services we provide are extremely small and very limited as is our physical presence. Monroe, La. But on Tuesday the company said it could no longer justify that stance. ru) from the Internet.

Adam Shostack
MARCH 19, 2020
One method discussed in a few talks (and I reference in mine) is having devs fill out self-service security questionnaires that provide some detail about the purpose of the service / new feature, what sensitive data it touches, potentially dangerous functionality it might have, etc. So what do you focus on? But what are those?

Krebs on Security
AUGUST 12, 2020
Postal Service, the credit bureaus or the Social Security Administration, it’s a good idea to do so for several reasons. Adding multi-factor authentication (MFA) at these various providers (where available) and/or establishing a customer-specific personal identification number (PIN) also can help secure online access.

Krebs on Security
NOVEMBER 21, 2018
Postal Service just fixed a security weakness that allowed anyone who has an account at usps.com to view account details for some 60 million other users, and in some cases to modify account details on their behalf. Image: USPS.com. The researcher said he informed the USPS about his finding more than a year ago yet never received a response.

Security Affairs
AUGUST 22, 2020
The flaws that could have allowed crooks to modify the amount of money they deposited on their card, so-called Deposit forgery, and make fraudulent cash withdrawals abusing of the new account balance. . An attacker with physical access to internal ATM components may be able to exploit this vulnerability to commit deposit forgery.”

Krebs on Security
APRIL 30, 2020
But apparently a number of criminal reshipping services are reporting difficulties due to the increased wait time when calling FedEx or UPS (to divert carded goods that merchants end up shipping to the cardholder’s address instead of to the mule’s). ” Alex Holden , founder and CTO of Hold Security , agreed. .

Krebs on Security
JANUARY 10, 2024
A California man who lost $100,000 in a 2021 SIM-swapping attack is suing the unknown holder of a cryptocurrency wallet that harbors his stolen funds. Experts say the development could make it easier for victims of crypto heists to recover stolen funds through the courts without having to wait years for law enforcement to take notice or help.

Schneier on Security
AUGUST 28, 2019
They affect national security. They're critical to national security as well as personal security. That started to change in the 1980s, when consumer electronics started to become the place where innovation happened. And it would be foolish to weaken them, even at the request of law enforcement.

Jane Frankland
OCTOBER 10, 2023
We all know the feeling: ensuring that your business is secure and running efficiently can feel overwhelming. It’s a hard balancing act between protecting valuable data, increasing productivity, controlling costs – especially when technology often seems to be outpacing security measures.

Malwarebytes
JUNE 9, 2022
Because more and more organizations have begun using VMs for cost-effectiveness and easier management of devices, this change in tactic makes sense. Software can be characterized as “bare metal” if installed directly onto the physical machine, between the hardware and the operating system. On Linux: BlackBasta 101.

eSecurity Planet
APRIL 29, 2024
Meanwhile, a 911 (or 999) call center’s objectives will probably focus on high availability of services and quick response times for callers. The 911 call center would be more concerned about utility disruption (electricity, phone) or a computer system crash that disrupts their ability to dispatch appropriate emergency responses.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?

Let's personalize your content