Prioritizing Vulnerabilities: A Growing Imperative
Security Boulevard
MARCH 29, 2024
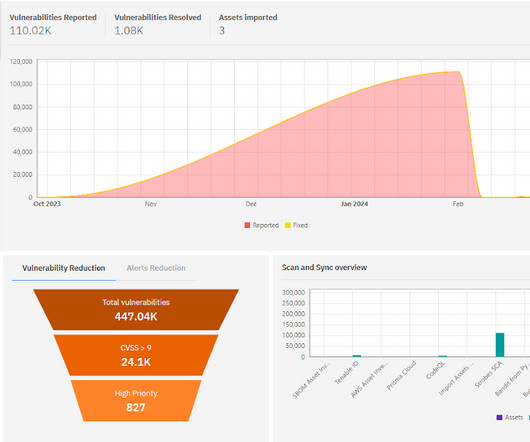
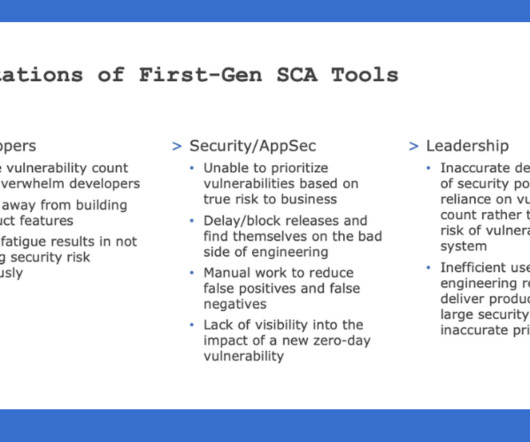
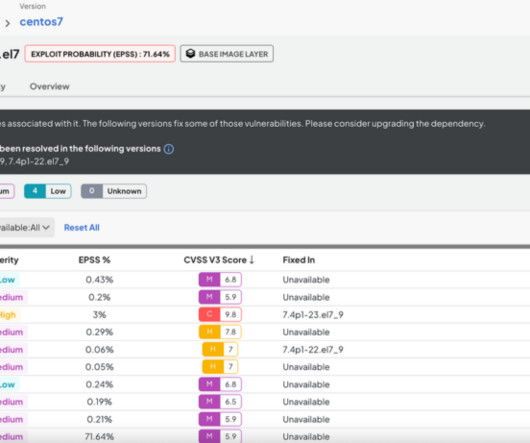
The post Prioritizing Vulnerabilities: A Growing Imperative appeared first on Strobes Security. The post Prioritizing Vulnerabilities: A Growing Imperative appeared first on Security Boulevard. It’s a harsh reality for many companies.














































Let's personalize your content