GUEST ESSAY: The role advanced ‘VM’ is ideally suited to play in combating modern cyber attacks
The Last Watchdog
APRIL 3, 2023
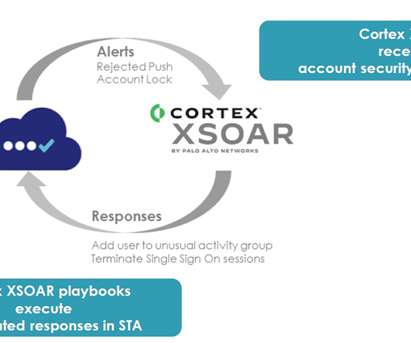
But advanced VM provides an actionable way of adhering to regulations and policies mandates that call for risks to be identified and detected as part of ongoing data security. Without automation, the laborious task of scanning and remediation is difficult. With traditional VM, achieving compliance is a struggle.














































Let's personalize your content