Threat landscape for industrial automation systems. H2 2023
SecureList
MARCH 19, 2024
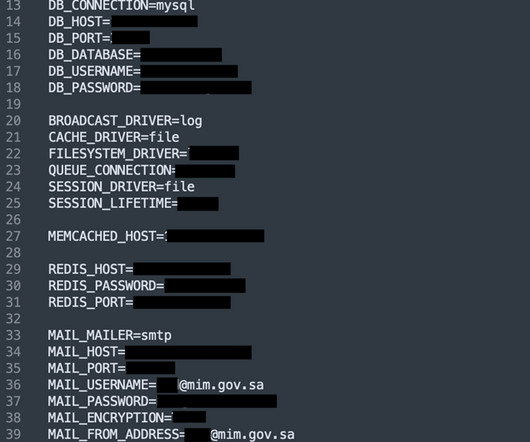
Global statistics across all threats In the second half of 2023, the percentage of ICS computers on which malicious objects were blocked decreased by 2.1 In the second half of 2023, the percentage of ICS computers on which malicious objects were blocked dropped for each of the main sources. pp to 31.9%. in Africa to 14.8%












































Let's personalize your content