‘The Manipulaters’ Improve Phishing, Still Fail at Opsec
Krebs on Security
APRIL 3, 2024
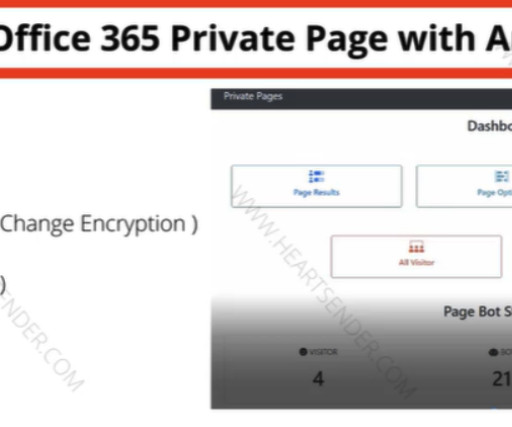
Manipulaters advertisement for “Office 365 Private Page with Antibot” phishing kit sold on the domain heartsender,com. The term “FUD” in those names stands for “ F ully U n- D etectable,” and it refers to cybercrime resources that will evade detection by security tools like antivirus software or anti-spam appliances.














































Let's personalize your content