Tips for Reverse-Engineering Malicious Code
Lenny Zeltser
SEPTEMBER 7, 2017
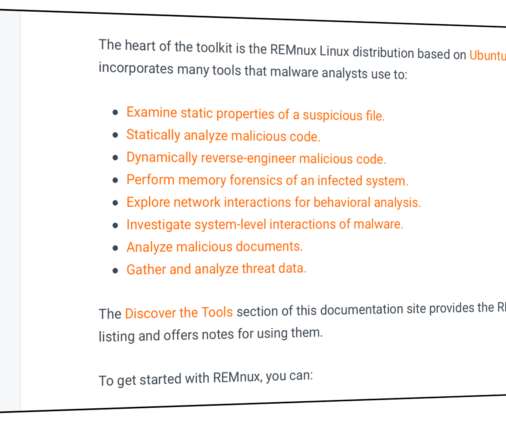
This cheat sheet outlines tips for reversing malicious Windows executables via static and dynamic code analysis with the help of a debugger and a disassembler. Overview of the Code Analysis Process. Identify strings and API calls that highlight the program’s suspicious or malicious capabilities.






















Let's personalize your content