How to Protect Your Machine Learning Models
Thales Cloud Protection & Licensing
FEBRUARY 14, 2024
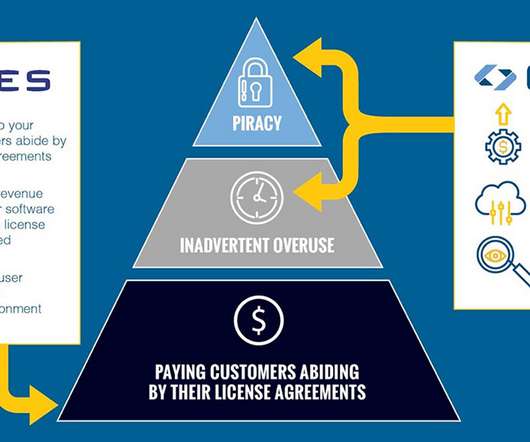
How to Protect Your Machine Learning Models madhav Thu, 02/15/2024 - 07:20 Contributors: Dr. Werner Dondl and Michael Zunke Introduction In computer technology, few fields have garnered as much attention as artificial intelligence ( AI) and machine learning (ML). One attack is a classic software copy attack.

















Let's personalize your content