Malicious USB drives are being posted to businesses
Security Boulevard
JANUARY 13, 2022
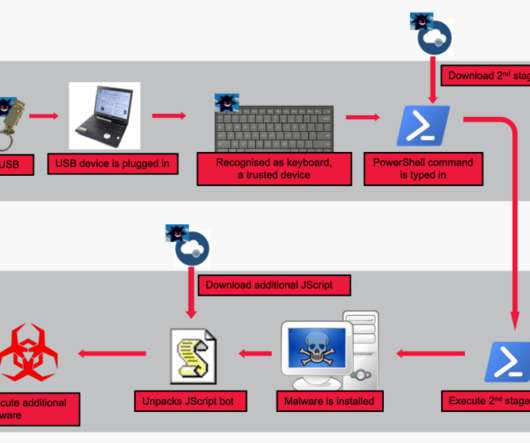
A notorious cybercrime gang, involved in a series of high profile ransomware attacks, has in recent months been sending out poisoned USB devices to US organisations. The post Malicious USB drives are being posted to businesses appeared first on The State of Security.






















Let's personalize your content