“FudCo” Spam Empire Tied to Pakistani Software Firm
Krebs on Security
SEPTEMBER 6, 2021
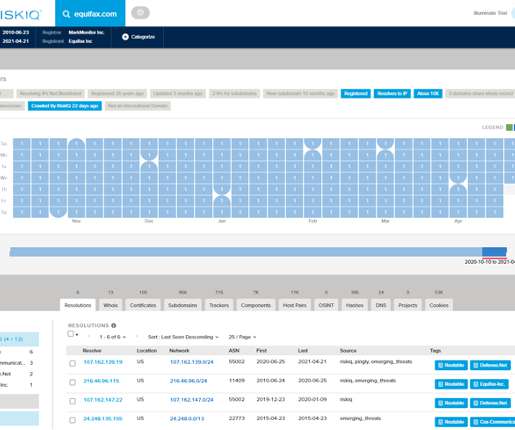
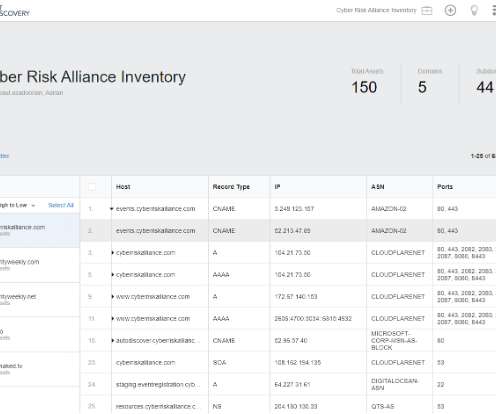
Six years later, a review of the social media postings from this group shows they are prospering, while rather poorly hiding their activities behind a software development firm in Lahore that has secretly enabled an entire generation of spammers and scammers.
























Let's personalize your content