Google TAG Warns of North Korean-linked ARCHIPELAGO Cyberattacks
The Hacker News
APRIL 5, 2023
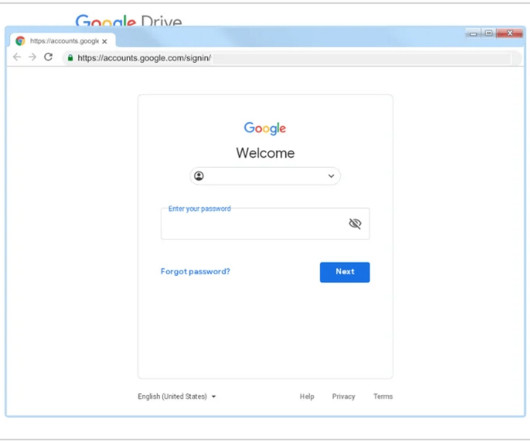
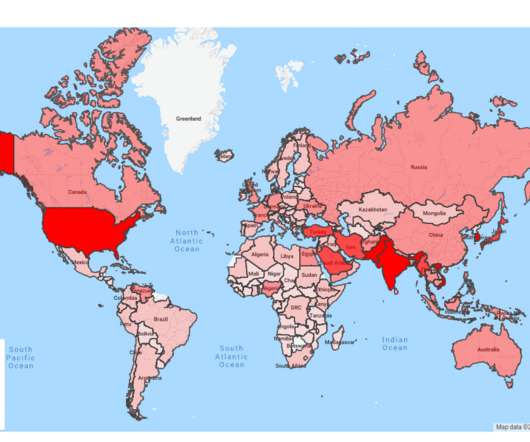
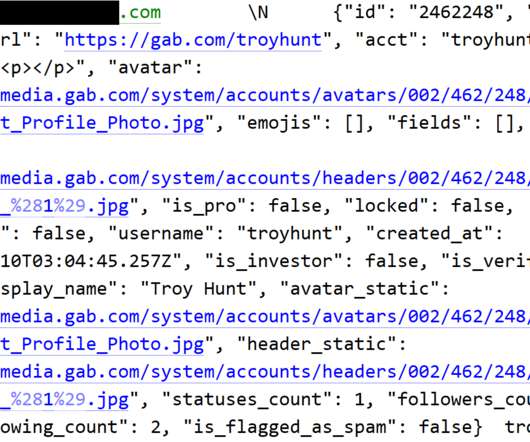
A North Korean government-backed threat actor has been linked to attacks targeting government and military personnel, think tanks, policy makers, academics, and researchers in South Korea and the U.S. The tech giant























Let's personalize your content