Intel and Check Point Software extend partnership for ransomware protection
CyberSecurity Insiders
JANUARY 3, 2023
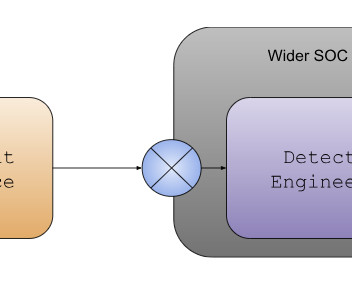
So, as a part of this collaboration the Harmony Endpoint solution from Check Point will be integrated into Intel vPro’s AI and ML driven threat detection tech allowing CPUs manufactured by the silicon wafer making giant analyze pre-detect data encryption commands in the digital attack flow.









































Let's personalize your content