Attackers use Google Calendar RAT to abuse Calendar service as C2 infrastructure
Security Affairs
NOVEMBER 6, 2023
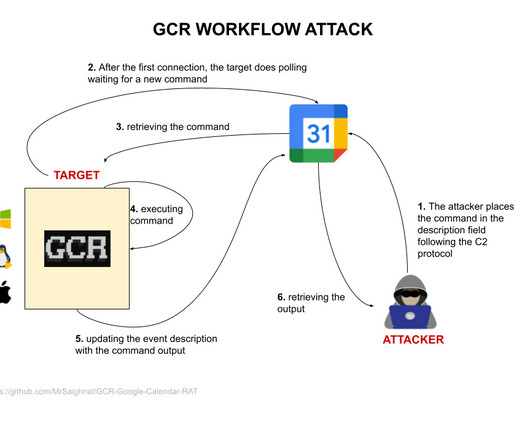
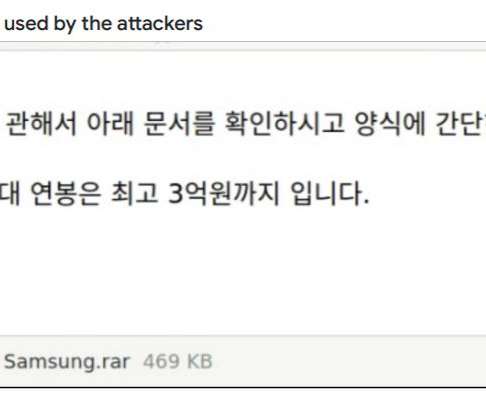
Google warns of multiple threat actors that are leveraging its Calendar service as a command-and-control (C2) infrastructure. Google warns of multiple threat actors sharing a public proof-of-concept (PoC) exploit, named Google Calendar RAT, that relies on Calendar service to host command-and-control (C2) infrastructure.















Let's personalize your content