C2 and the Docker Dance: Mythic 3.0’s Marvelous Microservice Moves
Security Boulevard
MAY 10, 2023
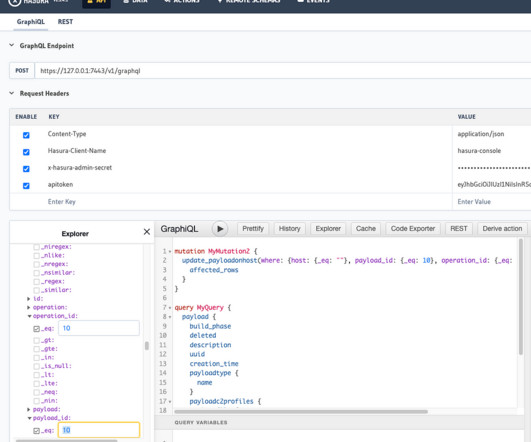
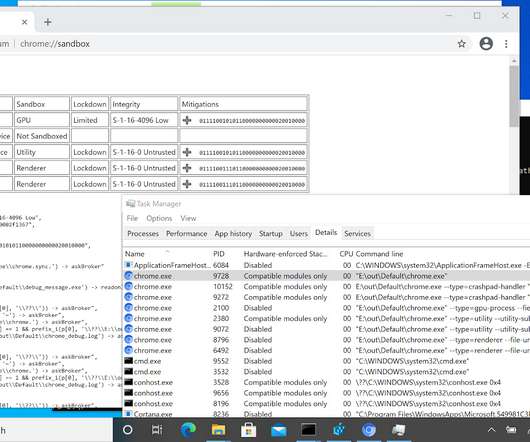
Mythic is a plug-n-play command and control (C2) framework that heavily leverages Docker and a microservice architecture where new agents, communication channels, and modifications can happen on the fly. Why the update? Why the big update to 3.0 instead of 2.4? Mythic 2.3 So, it became a perfect opportunity for a complete rewrite.















Let's personalize your content