Mitigating Dynamic Application Risks with Secure Firewall Application Detectors
Cisco Security
SEPTEMBER 23, 2021
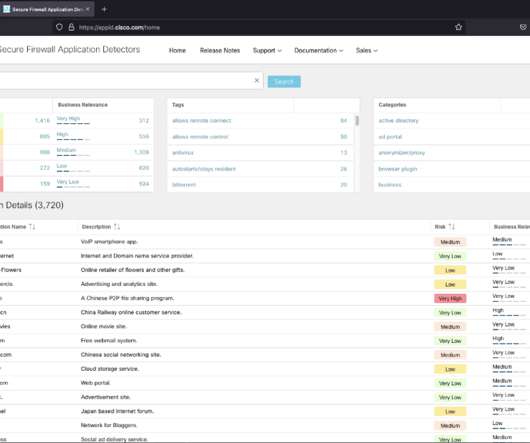
Enforce quality-of-service (QoS) policies and service guarantees for latency-sensitive applications (such as voice over IP [VoIP] and interactive gaming). Tags – Predefined tags that provide additional information about the application. Example tags include webmail, SSL protocol, file sharing/transfer, and displays ads.














Let's personalize your content