4 over-hyped security vulnerabilities of 2022
Malwarebytes
DECEMBER 18, 2022
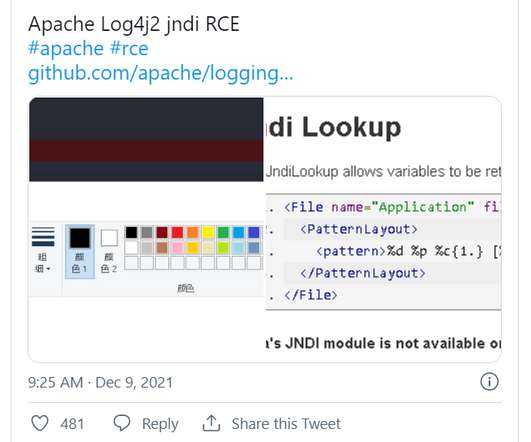
A critical vulnerability can send countless organizations into chaos, as security teams read up on the vulnerability, try to figure out whether it applies to their systems, download any potential patches, and deploy those fixes to affected machines. This makes the growth potential of an infection exponential. Essential building blocks.



















Let's personalize your content