What Matters Most: Remediating Vulnerabilities
NopSec
MARCH 18, 2016
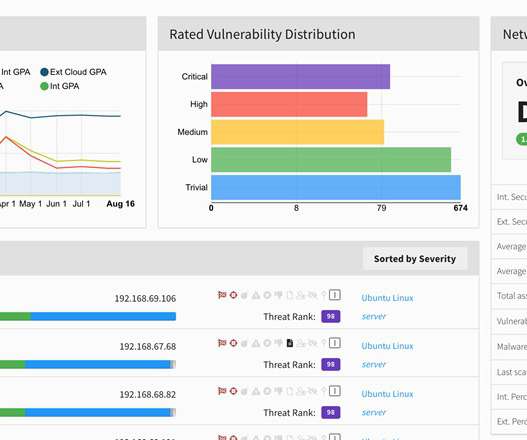
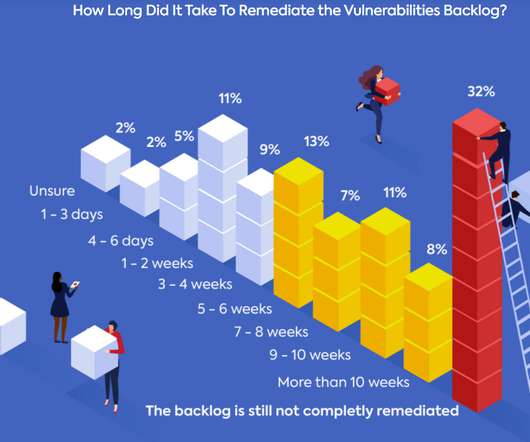
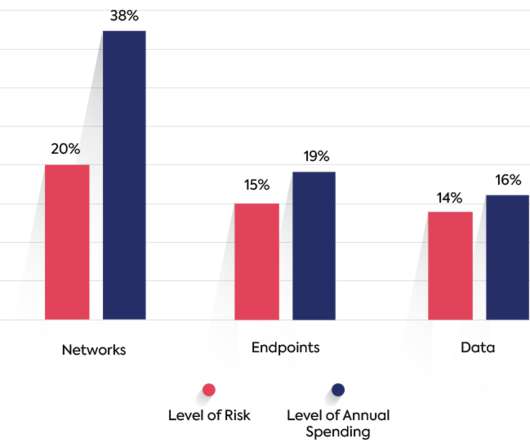
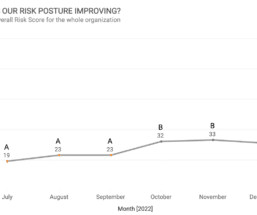
Scanning is an important part of a well-established vulnerability risk management program. Vulnerability scanners allow you to identify the threats and weaknesses in your network. You don’t want to spend your time going after minor issues when you could have bigger vulnerabilities just waiting to implode. Unified VRM 4.0














































Let's personalize your content