Anton’s Alert Fatigue: The Study
Anton on Security
NOVEMBER 6, 2024
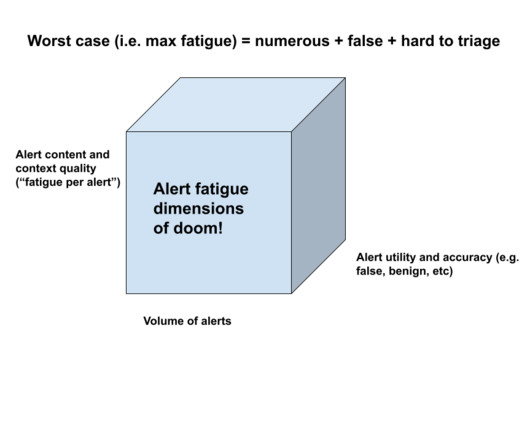
Now, take your time machine to 2002. An easy answer I get from many industry colleagues is that we could have easily solved the problem at 2002 levels of data volumes, environment complexity and threat activity. Mention “alert fatigue” to a SOC analyst. They would immediately recognize what you are talking about. Nah, didn’t do it.















































Let's personalize your content