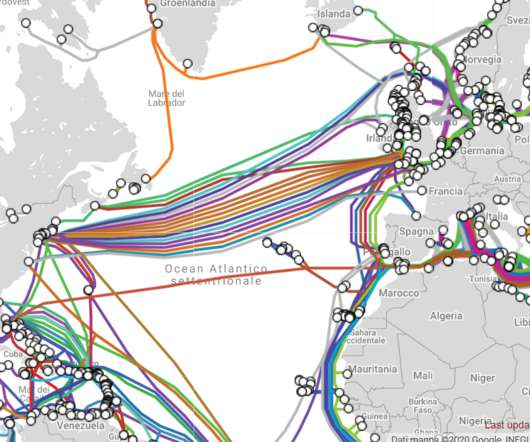
Russian spies are attempting to tap transatlantic undersea cables
Security Affairs
MARCH 1, 2020
The Register reports that the secret structures of GCHQ are part of the surveillance programme codenamed “CIRCUIT” and also refers to an Overseas Processing Centre 1 (OPC-1), while another centre, OPC-2, has been planned, according to documents leaked by Snowden. In the documents, the company is referred to as a “partner” codenamed Gerontic.












Let's personalize your content