The Now-Defunct Firms Behind 8chan, QAnon
Krebs on Security
OCTOBER 22, 2020
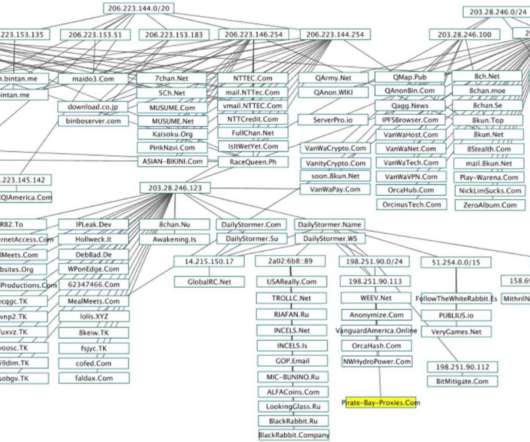
Some of the world’s largest Internet firms have taken steps to crack down on disinformation spread by QAnon conspiracy theorists and the hate-filled anonymous message board 8chan. Technology Inc. Technology Inc. Technology gives the latter the right to use more than 21,500 IP addresses. ” and “207.”










































Let's personalize your content