Ebury botnet malware infected 400,000 Linux servers since 2009
Bleeping Computer
MAY 14, 2024
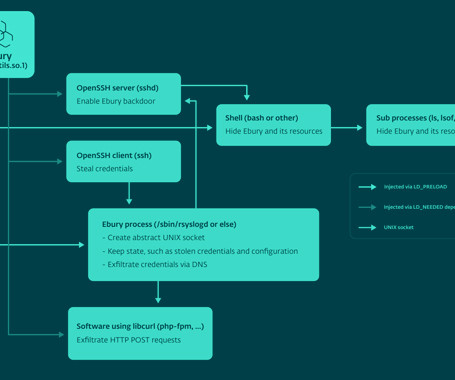
A malware botnet known as 'Ebury' has infected almost 400,000 Linux servers since 2009, with roughly 100,000 still compromised as of late 2023.
This site uses cookies to improve your experience. By viewing our content, you are accepting the use of cookies. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country we will assume you are from the United States. View our privacy policy and terms of use.

Bleeping Computer
MAY 14, 2024
A malware botnet known as 'Ebury' has infected almost 400,000 Linux servers since 2009, with roughly 100,000 still compromised as of late 2023.
The Hacker News
MAY 15, 2024
A malware botnet called Ebury is estimated to have compromised 400,000 Linux servers since 2009, out of which more than 100,000 were still compromised as of late 2023. The findings come from Slovak cybersecurity firm ESET, which characterized it as one of the most advanced server-side malware campaigns for financial gain.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Krebs on Security
JUNE 21, 2023
If you operate a cybercrime business that relies on disseminating malicious software, you probably also spend a good deal of time trying to disguise or “crypt” your malware so that it appears benign to antivirus and security products. This story explores the history and identity behind Cryptor[.]biz WHO RUNS CRYPTOR[.]BIZ?

The Hacker News
FEBRUARY 17, 2024
to his role in two different malware schemes, Zeus and IcedID, between May 2009 and February 2021. A Ukrainian national has pleaded guilty in the U.S. Vyacheslav Igorevich Penchukov (aka Vyacheslav Igoravich Andreev, father, and tank), 37, was arrested by Swiss authorities in October 2022 and extradited to the U.S.

Security Boulevard
MAY 15, 2024
The operators behind the Ebury server-side malware botnet have been doing business since at least 2009 and, according to the threat researchers who have been tracking it for the last decade, are stronger and more active than ever. The malware has compromised at least 400,000 Linux servers over the past 15 years, with about 100,000.

Krebs on Security
JULY 25, 2023
Now new findings reveal that AVrecon is the malware engine behind a 12-year-old service called SocksEscort , which rents hacked residential and small business devices to cybercriminals looking to hide their true location online. ” According to Kilmer, AVrecon is the malware that gives SocksEscort its proxies.

Krebs on Security
JUNE 1, 2023
This post is a deep dive on “ Megatraffer ,” a veteran Russian hacker who has practically cornered the underground market for malware focused code-signing certificates since 2015. More recently, it appears Megatraffer has been working with ransomware groups to help improve the stealth of their malware. WHO IS MEGATRAFFER?

Security Affairs
FEBRUARY 17, 2024
Ukrainian national Vyacheslav Igorevich Penchukov has pleaded guilty to his key roles in the Zeus and IcedID malware operations. Vyacheslav Igorevich Penchukov was a leader of two prolific malware groups that infected thousands of computers with malicious software.

The Hacker News
DECEMBER 1, 2021
A Russian national charged with providing bulletproof hosting services for cybercriminals, who used the platform to spread malware and attack U.S. organizations and financial institutions between 2009 to 2015, has received a 60-month prison sentence.
Malwarebytes
DECEMBER 5, 2022
It's been active since 2009 and is responsible for many high profile attacks. Now, researchers at Volexity have analyzed a new campaign that is likely targeting cryptocurrency users and organizations with a variant of the AppleJeus malware by using malicious Microsoft Office documents. Lazarus Group. Second wave. Be careful.

The Hacker News
OCTOBER 21, 2021
for offering "bulletproof hosting" services to cybercriminals, who used the technical infrastructure to distribute malware and attack financial institutions across the country between 2009 to 2015. Two Eastern European nationals have been sentenced in the U.S.
Security Affairs
NOVEMBER 16, 2020
The activity of the Lazarus APT group surged in 2014 and 2015, its members used mostly custom-tailored malware in their attacks. This threat actor has been active since at least 2009, possibly as early as 2007, and it was involved in both cyber espionage campaigns and sabotage activities aimed to destroy data and disrupt systems.

Security Affairs
MARCH 28, 2019
The activity of the Lazarus Group surged in 2014 and 2015, its members used mostly custom-tailored malware in their attacks and experts that investigated on the crew consider it highly sophisticated. At the time, North Korea-linked Lazarus APT group leveraged for the first time on a MacOS variant of the Fallchill malware.

Security Affairs
AUGUST 10, 2018
Security researchers at Intezer and McAfee have conducted a joint investigation that allowed them to collect evidence that links malware families attributed to North Korean APT groups such as the notorious Lazarus Group and Group 123. Each node represents a malware family or a hacking tool (“ Brambul ,” “ Fallchill ,” etc.)
Security Affairs
DECEMBER 17, 2019
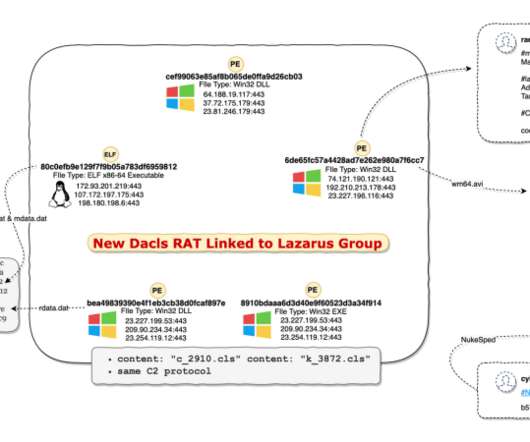
The activity of the Lazarus APT group (aka HIDDEN COBRA ) surged in 2014 and 2015, its members used mostly custom-tailored malware in their attacks. Dacls is the first malware linked to the Lazarus group that targets Linux systems. com ‘ was involved in past campaigns of the Lazarus APT. Pierluigi Paganini.

CyberSecurity Insiders
APRIL 26, 2023
Lookout, which established itself in business in 2009, offers Mobile Endpoint Security solutions with millions of users and hundreds of millions in funding. Although the financial terms are yet to be disclosed on an official note, unconfirmed sources state that the deal is to be valued at $224 million, all in cash.

Security Affairs
SEPTEMBER 22, 2018
Scan4you is a VirusTotal like online multi-engine antivirus scanning service that could be used by vxers to test evasion abilities of their malware against the major antiviruses. A second customer used Scan4you to contribute to the development of infamous Citadel malware that caused over $500 million in fraud-related losses.

Krebs on Security
DECEMBER 8, 2021
Darkode was taken down in 2015 as part of an FBI investigation sting operation , but screenshots of the community saved by this author show that DCReavers2 was already well known to the Darkode founders when his membership to the forum was accepted in May 2009. DCReavers2 was just the 22nd account to register on the Darkode cybercrime forum.

Krebs on Security
JANUARY 8, 2024
As detailed in my 2014 book, Spam Nation , Spamdot was home to crooks controlling some of the world’s nastiest botnets, global malware contagions that went by exotic names like Rustock , Cutwail , Mega-D , Festi , Waledac , and Grum. ” Likewise, the bulletproof domain service icamis[.]ws ws was registered to an Andrew Artz.
Threatpost
APRIL 11, 2022
The APT28 (Advanced persistence threat) is operating since 2009, this group has worked under different names such as Sofacy, Sednit, Strontium Storm, Fancy Bear, Iron Twilight, and Pawn.

The Last Watchdog
FEBRUARY 7, 2023
Related: Deploying human sensors Additionally, with tools like ChatGPT, almost anyone can create new malware and become a threat actor. Founded in 2009, Vade supplies AI-based cybersecurity technologies that help companies defend many types of email-borne attacks.
Security Affairs
AUGUST 8, 2022
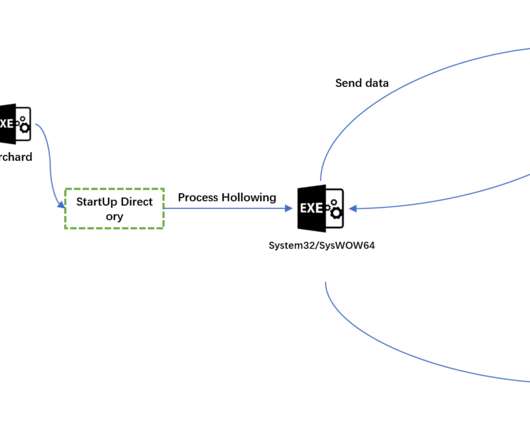
“It’s worth pointing out that the wallet address is the miner reward receiving address of the Bitcoin Genesis Block , which occurred on January 3, 2009, and is believed to be held by Nakamoto.” The bot allows operators to deploy additional malware onto the infected machine and execute commands received from the C2 server.

Security Affairs
OCTOBER 21, 2021
The United States Department of Justice sentenced two individuals that were providing bulletproof hosting to various malware operations. The two individuals, Aleksandr Skorodumov (33) of Lithuania, and Pavel Stassi (30) of Estonia, administrated the bulletproof hosting service between 2009 and 2015.

Security Affairs
APRIL 5, 2019
A few days ago, the researchers of ZLab Yoroi-Cybaze dissected another attack wave of the infamous Ursnif malware, also known as Gozi ISFB , an offspring of the original Gozi which source code was leaked in 2014. Ursnif/Gozi is active from over a decade and was one of the most active malware listed in 2017 and 2018.

CyberSecurity Insiders
MAY 6, 2021
Report released by the firm says that the discovered flaw is actually an amalgamation of 5 different flaws that are present on the Dell BIOS Utility Driver called DBUtil and has been in place since 2009.
Security Affairs
NOVEMBER 15, 2021
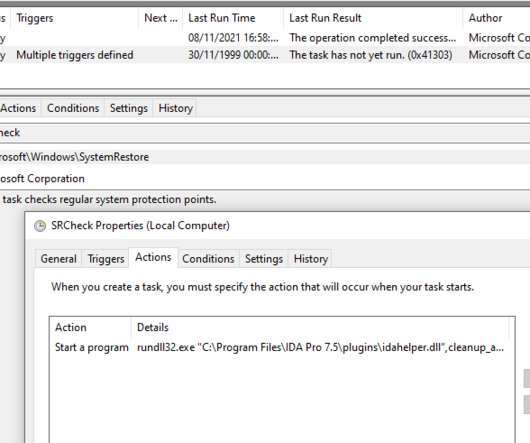
IDA Pro is widely used by malware researchers to translate machine-executable code into assembly language source code for purpose of debugging and reverse engineering. . The activity of the Lazarus APT group surged in 2014 and 2015, its members used mostly custom-tailored malware in their attacks. Win64/NukeSped.JS : devguardmap[.]org
Security Affairs
DECEMBER 25, 2020
The activity of the Lazarus APT group surged in 2014 and 2015, its members used mostly custom-tailored malware in their attacks. This threat actor has been active since at least 2009, possibly as early as 2007, and it was involved in both cyber espionage campaigns and sabotage activities aimed to destroy data and disrupt systems.

Security Affairs
OCTOBER 23, 2023
billion Aadhaars issued by the UIDAI since this ID service launched in 2009, this system represents one of the largest biometric ID programs on the planet, according to a report published by think tank Brookings Institution. With roughly 1.4
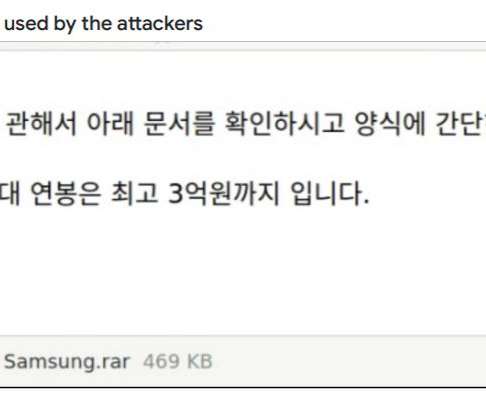
Security Affairs
NOVEMBER 28, 2021
North Korea-linked APT group posed as Samsung recruiters is a spear-phishing campaign that targeted South Korean security companies that sell anti-malware solutions, Google TAG researchers reported. The activity of the Zinc APT group, aka Lazarus , surged in 2014 and 2015, its members used mostly custom-tailored malware in their attacks.

Security Affairs
OCTOBER 27, 2021
The activity of the Lazarus APT group surged in 2014 and 2015, its members used mostly custom-tailored malware in their attacks. This threat actor has been active since at least 2009, possibly as early as 2007, and it was involved in both cyber espionage campaigns and sabotage activities aimed to destroy data and disrupt systems.

Security Affairs
JULY 6, 2021
According to Group-IB’s Threat Intelligence team, the suspect, dubbed Dr HeX by Group-IB based on one of the nicknames that he used, has been active since at least 2009 and is responsible for a number of cybercrimes, including phishing, defacing, malware development, fraud, and carding that resulted in thousands of unsuspecting victims.

SiteLock
AUGUST 27, 2021
Protecting yourself from phishing and malware attacks is not only important, it’s a fundamental Internet survival skill, made even more essential if you have a web presence you depend on. The.shtml file contained an iframe that loaded PHP from a legitimate site registered in 2009. Gee, thanks, Kyle. Legitimate, but compromised.

Krebs on Security
JULY 20, 2021
A federal judge in Connecticut today handed down a sentence of time served to spam kingpin Peter “Severa” Levashov , a prolific purveyor of malicious and junk email, and the creator of malware strains that infected millions of Microsoft computers globally. In this paid ad from 2004, Severa lists prices to rent his spam botnet.
Security Affairs
JANUARY 27, 2022
North Korea-linked Lazarus APT group uses Windows Update client to deliver malware on Windows systems. The activity of the Lazarus APT group surged in 2014 and 2015, its members used mostly custom-tailored malware in their attacks. The use of Github as a C2 aims at evading detection.

Malwarebytes
JULY 14, 2022
Securing that many endpoints can get really complex, really fast, especially when you consider that the common wisdom that Macs don’t get malware simply isn’t true: in fact, the number of malware detections on Mac jumped 200% year-on-year in 2021. And it’s not just malware you have to worry about with your Mac endpoints.

Security Affairs
NOVEMBER 5, 2019
In 2017, a hacker group known as the Shadow Brokers stolen malware and hacking tools from the arsenal of the NSA-Linked Equation Group , then it published online the data dump called “ Lost in Translation.” The DarkUniverse has been active at least from 2009 until 2017. dll malware module provides keylogging functionality.

Security Affairs
FEBRUARY 25, 2021
“Once the malicious document is opened, the malware is dropped and proceeds to the next stage of the deployment process. The ThreatNeedle malware used in this campaign belongs to a malware family known as Manuscrypt, which belongs to the Lazarus group and has previously been seen attacking cryptocurrency businesses.”
Security Affairs
JUNE 18, 2020
Researchers uncovered an ongoing campaign delivering the Qbot malware to steal credentials from customers of dozens of US financial institutions. Security researchers at F5 Labs have spotted ongoing attacks using Qbot malware payloads to steal credentials from customers of dozens of US financial institutions. Pierluigi Paganini.

eSecurity Planet
FEBRUARY 10, 2023
National Security Agency (NSA) in 2009, LookingGlass Cyber Solutions provides three threat intelligence analysis products: a threat intelligence platform ( scoutPrime ), a threat modeling tool ( scoutThreat ), and an attack surface monitoring solution ( scoutInspect ). Company Description Spun out from the U.S.

Krebs on Security
MARCH 22, 2022
When I first began writing about Vrublevsky in 2009 as a reporter for The Washington Post , ChronoPay and its sister firm Red & Partners (RNP) were earning millions setting up payment infrastructure for fake antivirus peddlers and spammers pimping male enhancement drugs.

Security Affairs
SEPTEMBER 9, 2019
The Thrip group used both custom malware and legitimate tools to hit its targets that continue to include defense contractors, telecoms companies, and satellite operators. This malware appears to be an evolution of an older Billbug tool known as Evora.” Security experts at Symantec speculate that Thrip is a sub-group of Billbug.
Security Affairs
FEBRUARY 9, 2023
-based financial institutions that occurred in 2009 and 2010, predating his involvement in Dyre or the Trickbot Group. Valentin Karyagin has been involved in the development of ransomware and other malware projects. Maksim Mikhailov has been involved in development activity for the Trickbot Group.

Security Affairs
JANUARY 16, 2019
The activity of the Lazarus Group surged in 2014 and 2015, its members used mostly custom-tailored malware in their attacks and experts that investigated on the crew consider it highly sophisticated. Last year, researchers revealed that code reuse links most North Korean malware to Lazarus. ” reported Flashpoint.

Security Affairs
NOVEMBER 10, 2018
Security experts from Symantec have discovered a malware, tracked as FastCash Trojan , that was used by the Lazarus APT Group , in a string of attacks against ATMs. The ATP group has been using this malware at least since 2016 to siphon millions of dollars from ATMs of small and midsize banks in Asia and Africa.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content