China-linked Budworm APT returns to target a US entity
Security Affairs
OCTOBER 13, 2022
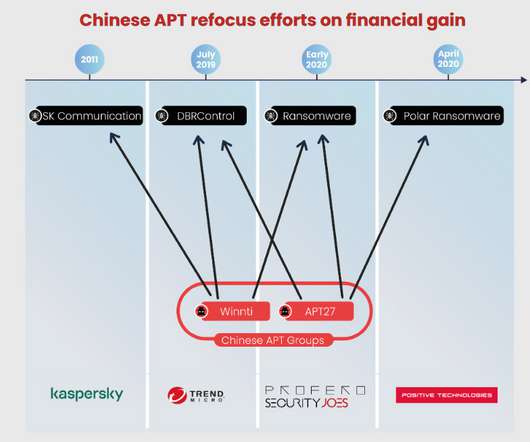
The China-linked APT27 group has been active since 2010, it targeted organizations worldwide, including U.S. The group was involved in cyber espionage campaigns aimed at new generation weapons and in surveillance activities on dissidents and other civilian groups. .” It is designed to load malicious DLLs and encrypt payloads.”











Let's personalize your content