MyBook Users Urged to Unplug Devices from Internet
Krebs on Security
JUNE 25, 2021
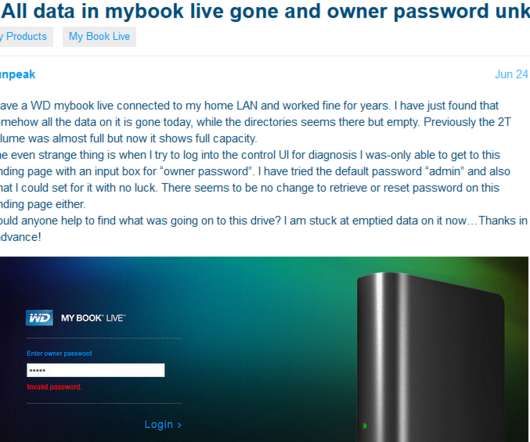
. “The vulnerability report CVE-2018-18472 affects My Book Live devices originally introduced to the market between 2010 and 2012,” reads a reply from Western Digital that Wizcase posted to its blog. “These products have been discontinued since 2014 and are no longer covered under our device software support lifecycle.
































Let's personalize your content