Researcher Exposes Inductive Automation Ignition Vulnerabilities: CVE-2023-39475 & 39476
Penetration Testing
JANUARY 4, 2024
In January 2010, Inductive Automation introduced the Ignition platform, an integrated software solution for SCADA systems.

Penetration Testing
JANUARY 4, 2024
In January 2010, Inductive Automation introduced the Ignition platform, an integrated software solution for SCADA systems.

SC Magazine
FEBRUARY 12, 2021
To understand the significance, there were far more “critical” and “high severity” vulnerabilities in 2020 (10,342) than the total number of all vulnerabilities recorded in 2010 (4,639), according to Redscan, which ran the analysis of NIST’s National Vulnerability Database (NVD).
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Security Affairs
OCTOBER 13, 2022
The China-linked APT27 group has been active since 2010, it targeted organizations worldwide, including U.S. It has legitimate uses as a penetration testing tool but is frequently exploited by malicious actors. This is the first time that Symantec researchers have observed the Budworm group targeting a U.S-based

SC Magazine
MARCH 29, 2021
CRISC Company: ISACA Noteworthy: Nearly 30,000 professionals have earned CRISC (Certified in Risk and Information Systems Control) since it was established in 2010, and the certification was fourth on Global Knowledge’s list of top-paying IT certifications for 2020. FINALIST | BEST PROFESSIONAL CERTIFICATION PROGRAM.

Security Affairs
OCTOBER 17, 2018
According to VirusTotal the software was “seen in the Wild” in 2010 but submitted only on 2018-10-12! I do have experience on security testing since I have been performing penetration testing on several US electronic voting systems. Stage4 is pretty interesting per-se. Maybe hash collision over multiple years?

SecureWorld News
JUNE 7, 2024
The evolving landscape of cyber warfare Historical precedents, such as the Stuxnet worm , which targeted and sabotaged Iran's nuclear enrichment facilities in 2010, highlight the devastating potential of cyberattacks on national security.
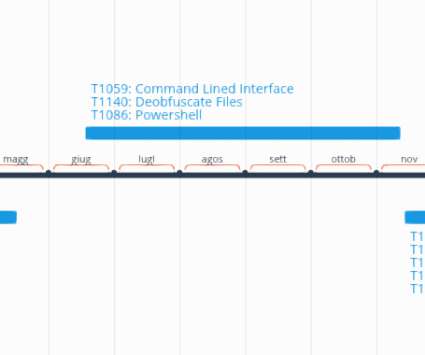
Security Affairs
DECEMBER 4, 2019
During my PhD program I worked for US Government (@ National Institute of Standards and Technology, Security Division) where I did intensive researches in Malware evasion techniques and penetration testing of electronic voting systems.
Let's personalize your content