YTStealer info-stealing malware targets YouTube content creators
Security Affairs
JUNE 29, 2022
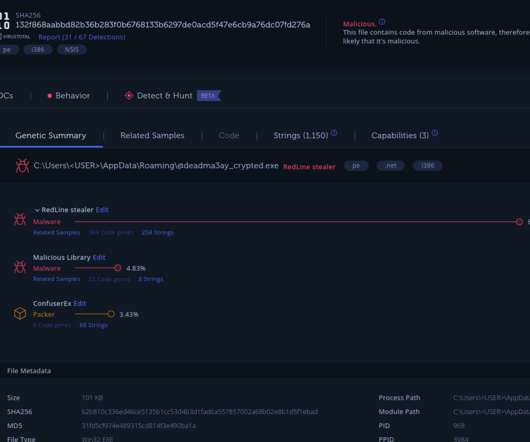
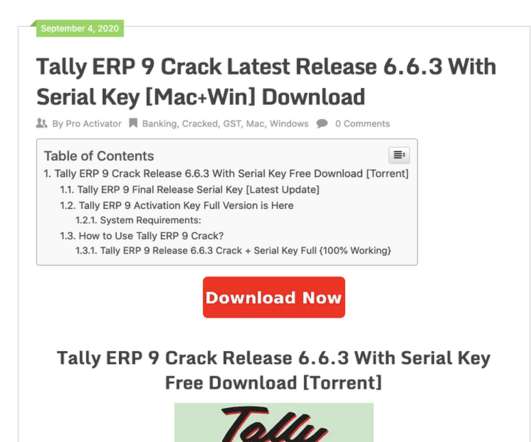
Researchers detailed a new information-stealing malware, dubbed YTStealer, that targets YouTube content creators. Intezer cybersecurity researchers have detailed a new information-stealing malware, dubbed YTStealer, that was developed to steal authentication cookies from YouTube content creators.





















Let's personalize your content