DePriMon downloader uses a never seen installation technique
Security Affairs
NOVEMBER 21, 2019
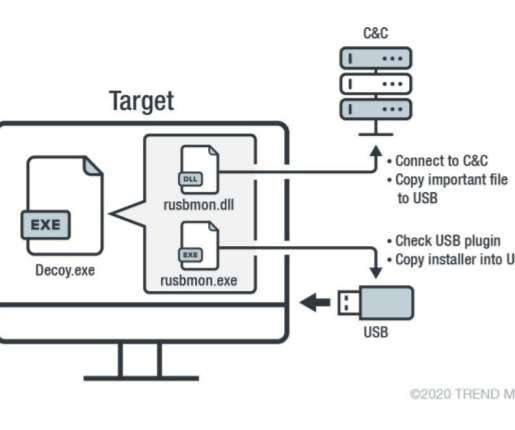
The new DePriMon downloader was used by the Lambert APT group, aka Longhorn, to deploy malware. According to a report published by Symantec in 2017, Longhorn is a North American hacking group that has been active since at least 2011. We believe DePriMon is the first example of malware using this technique ever publicly described.”









Let's personalize your content