Tracking the Cost of Quantum Factoring
Google Security
MAY 23, 2025
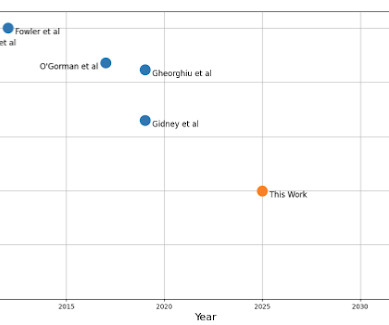
National Institute of Standards and Technology (NIST) and others in government, industry, and academia to develop and transition to post-quantum cryptography (PQC), which is expected to be resistant to quantum computing attacks. Google has long worked with the U.S. For signatures, things are more complex.









































Let's personalize your content