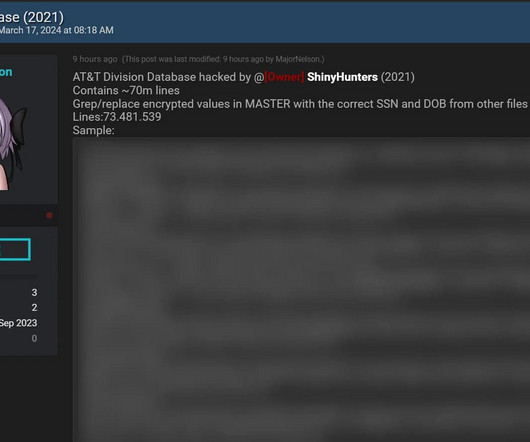
Russians Hack FBI Comms System
Schneier on Security
SEPTEMBER 24, 2019
intelligence communications, including hacking into computers not connected to the internet. It's unclear whether the Russians were able to recover encrypted data or just perform traffic analysis. Its poor design just encourages users to turn off the encryption. counterintelligence vulnerabilities.





































Let's personalize your content