SHARED INTEL: How ransomware evolved from consumer trickery to deep enterprise hacks
The Last Watchdog
JUNE 21, 2020
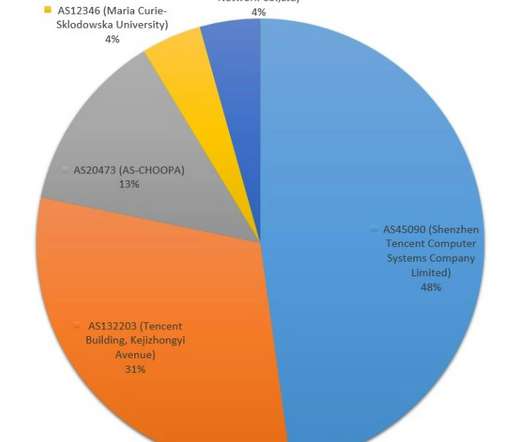
Although most people think of ransomware as a dodgy application that encrypts data and holds it for ransom, the concept is much more heterogeneous than that. The Archiveus Trojan from 2006 was the first one to use RSA cipher, but it was reminiscent of a proof of concept and used a static 30-digit decryption password that was shortly cracked.






























Let's personalize your content