North Korea-linked APT37 exploited IE zero-day in a recent attack
Security Affairs
OCTOBER 19, 2024
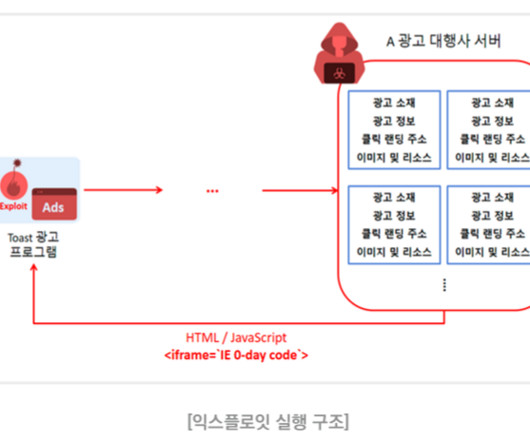
North Korea-linked group APT37 exploited an Internet Explorer zero-day vulnerability in a supply chain attack. “Successful exploitation of this vulnerability requires an attacker to first prepare the target so that it uses Edge in Internet Explorer Mode.”
































Let's personalize your content