Return of the MINEBRIDGE RAT With New TTPs and Social Engineering Lures
Security Boulevard
FEBRUARY 23, 2021
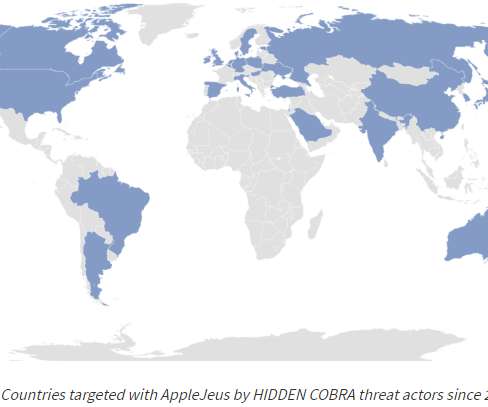
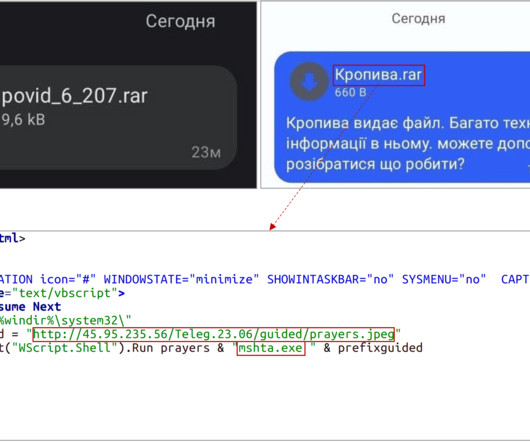
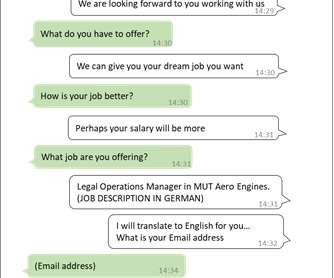
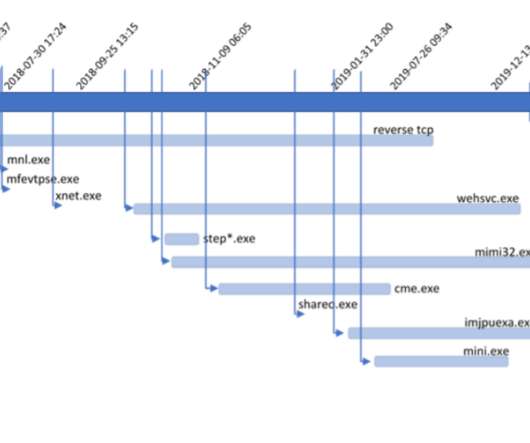
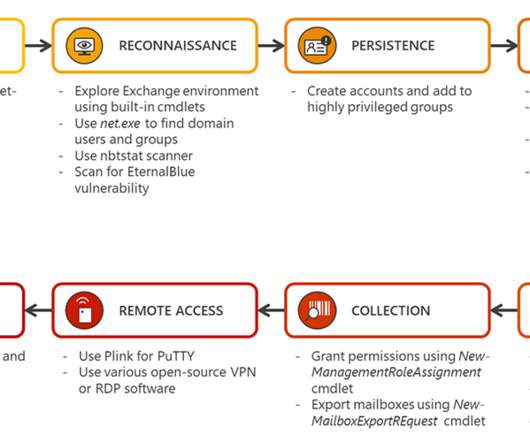
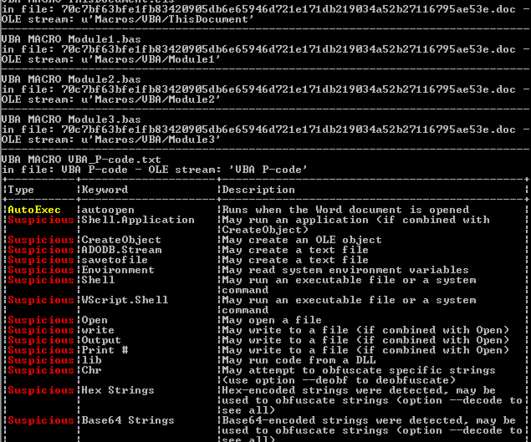
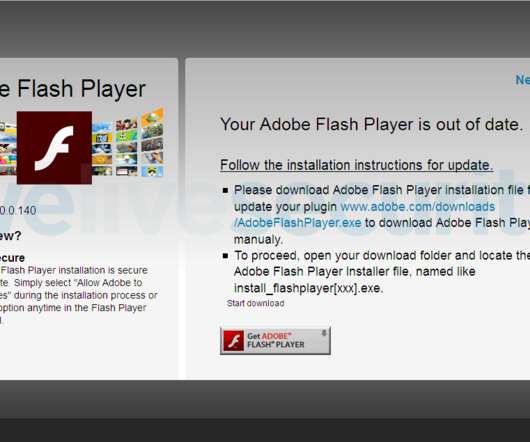
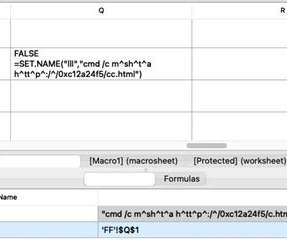
Such lures are used as social engineering schemes by threat actors; in this case, the malware was targeted at security researchers. We have recently observed other instances of threat actors targeting security researchers with social engineering techniques. Threat attribution. Currently logged in user name.































Let's personalize your content