Phishing Sites Targeting Scammers and Thieves
Krebs on Security
AUGUST 9, 2021
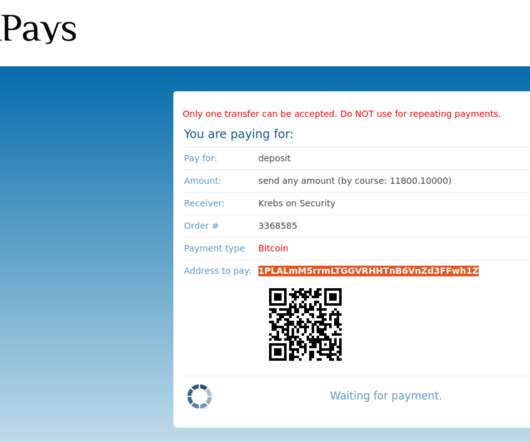
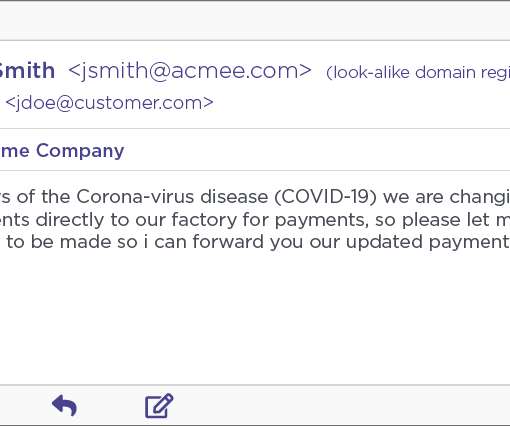
That was right after KrebsOnSecurity broke the news that someone had hacked BriansClub and siphoned information on 26 million stolen debit and credit accounts. com, and was wondering when the funds would be reflected in the balance of his account on the shop. Shortly after it came online as a phishing site last year, BriansClub[.]com





































Let's personalize your content