Anubis, a new info-stealing malware spreads in the wild
Security Affairs
AUGUST 27, 2020
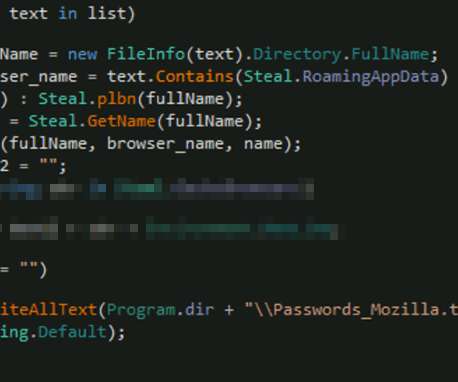
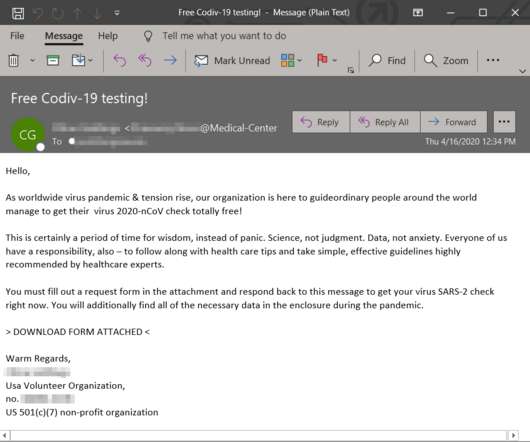
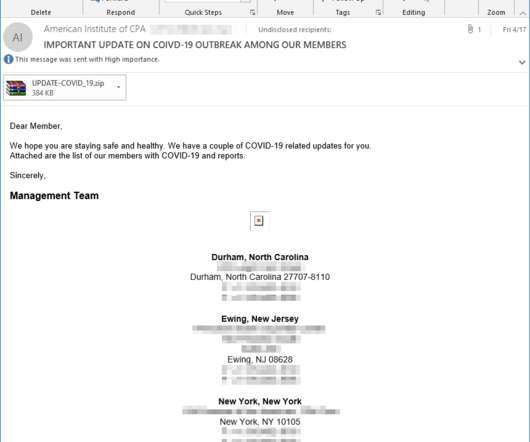
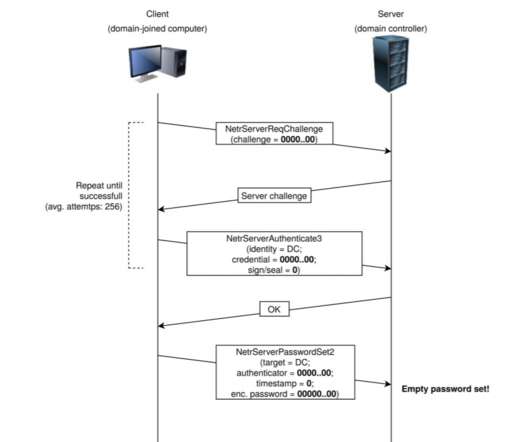
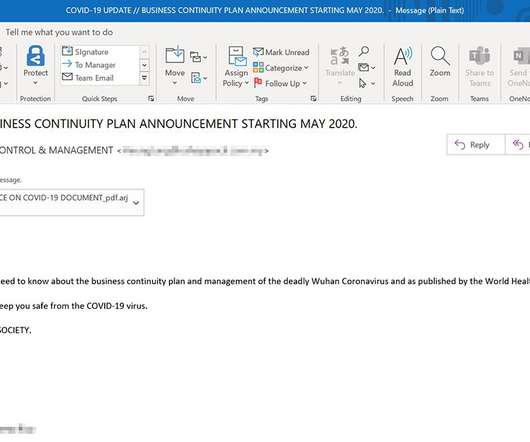
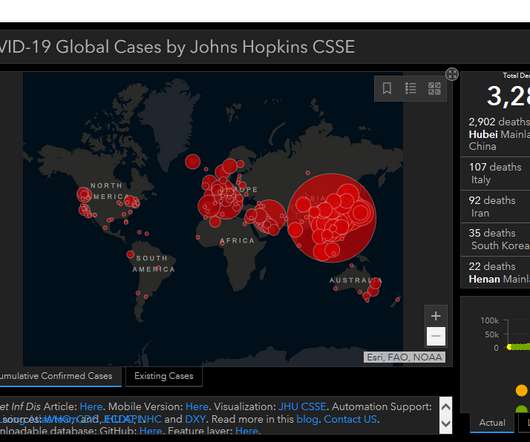
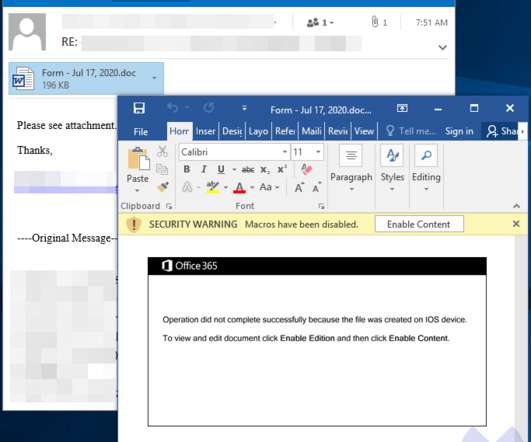
Microsoft warned of a recently uncovered piece of malware, tracked as Anubis that was designed to steal information from infected systems. This week, Microsoft warned of a recently uncovered piece of malware, tracked as Anubis, that was distributed in the wild to steal information from infected systems. Pierluigi Paganini.























Let's personalize your content