TrickGate, a packer used by malware to evade detection since 2016
Security Affairs
JANUARY 31, 2023
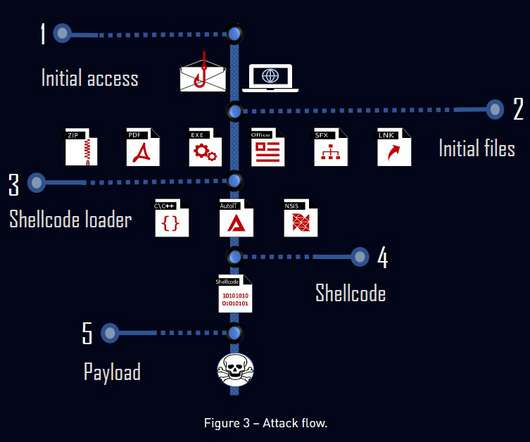
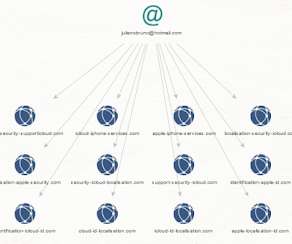
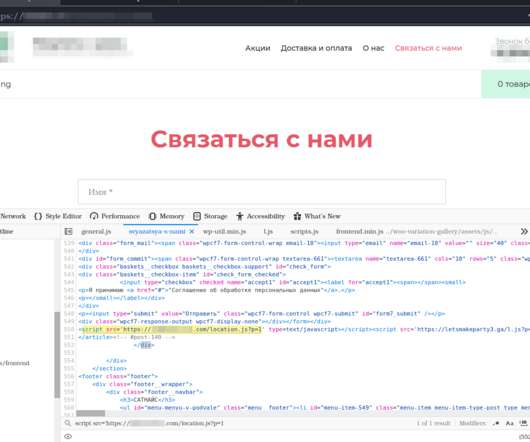
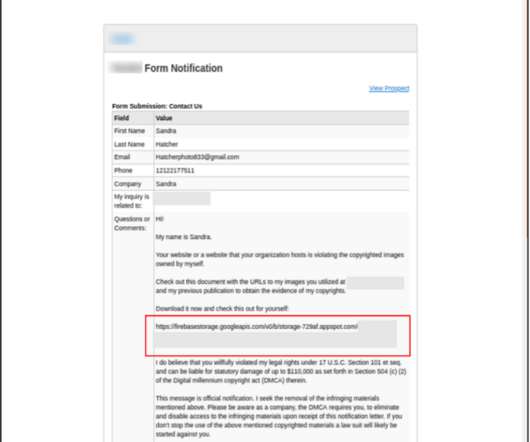
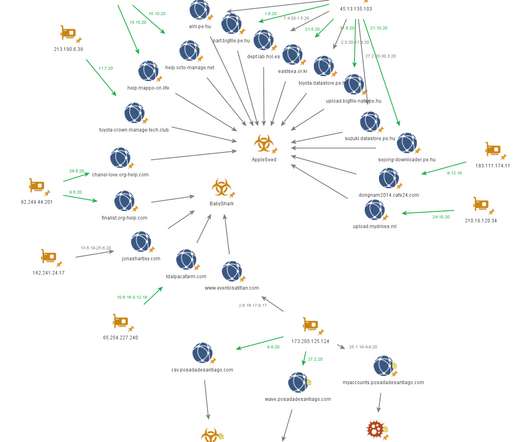
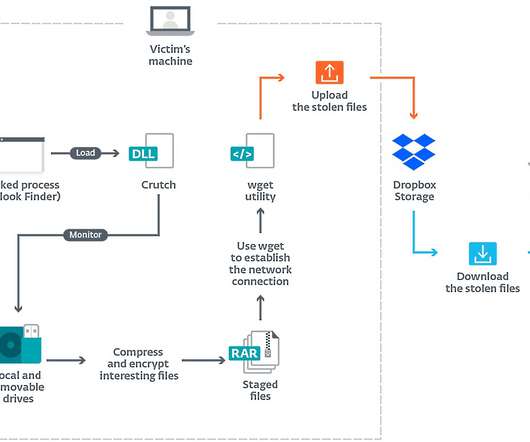
TrickGate is a shellcode-based packer offered as a service to malware authors to avoid detection, CheckPoint researchers reported. TrickGate is a shellcode-based packer offered as a service, which is used at least since July 2016, to hide malware from defense programs. ” concludes the report.





































Let's personalize your content