Who’s Behind the NetWire Remote Access Trojan?
Krebs on Security
MARCH 9, 2023
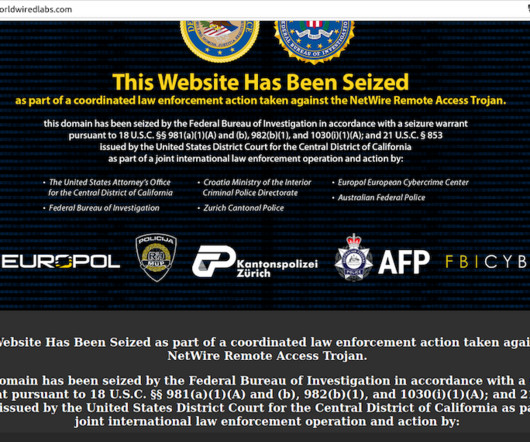
A Croatian national has been arrested for allegedly operating NetWire , a Remote Access Trojan (RAT) marketed on cybercrime forums since 2012 as a stealthy way to spy on infected systems and siphon passwords. A review of DNS records for both printschoolmedia[.]org DNS records for worldwiredlabs[.]com org and wwlabshosting[.]com


































Let's personalize your content