Who’s Behind the RevCode WebMonitor RAT?
Krebs on Security
APRIL 22, 2019
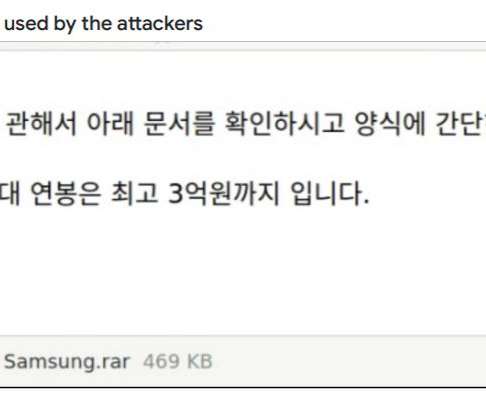
The software is broadly classified as malware by most antivirus companies, likely thanks to an advertised feature list that includes dumping the remote computer’s temporary memory; retrieving passwords from dozens of email programs; snarfing the target’s Wi-Fi credentials; and viewing the target’s Webcam.






































Let's personalize your content