GhostRace – New Data Leak Vulnerability Affects Modern CPUs
The Hacker News
MARCH 15, 2024
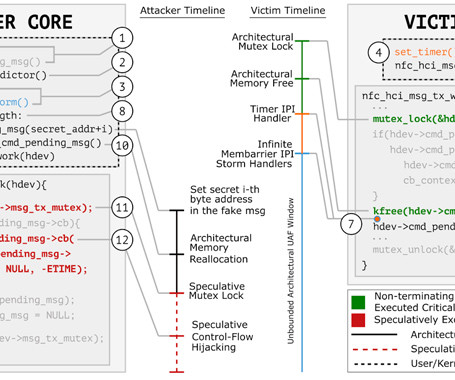
A group of researchers has discovered a new data leakage attack impacting modern CPU architectures supporting speculative execution. Dubbed GhostRace (CVE-2024-2193), it is a variation of the transient execution CPU vulnerability known as Spectre v1 (CVE-2017-5753). The approach combines speculative execution and race conditions.













































Let's personalize your content