Researchers Warn of Exploit that Bypasses Web Application Firewalls
eSecurity Planet
DECEMBER 12, 2022
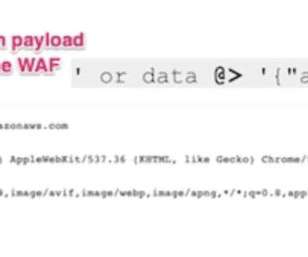
Team82 researchers have disclosed an attack technique that bypasses industry-leading web application firewalls (WAFs) by appending JSON syntax to SQL injection payloads. The researchers used a WAF shortcoming against the firewalls: Lack of support for native JSON syntax. Read next: Top Database Security Solutions.





















Let's personalize your content