When Low-Tech Hacks Cause High-Impact Breaches
Krebs on Security
FEBRUARY 26, 2023
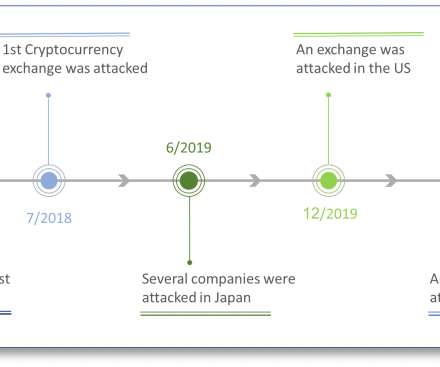
Media coverage understandably focused on GoDaddy’s admission that it suffered three different cyberattacks over as many years at the hands of the same hacking group. But both SMS and app-based codes can be undermined by phishing attacks that simply request this information in addition to the user’s password.









































Let's personalize your content